The threat landscape report from BGD e-GOV CIRT shows a significant 71.39% increase in malware infections linked to potential ransomware threats.
The report shows that there exist vulnerabilities in Bangladesh that could lead to ransomware attacks on various organizations. The main malware strains identified are M0yv, Phorpiex, and Necurs, which can trigger different types of ransomware attacks such as Maze, Avaddon, Grandcab, and Locky.
CIRT found many attempts related to Indicators of Compromise (IOCs) of Mallox Ransomware. These attempts focused mainly on exploiting weaknesses in Mysql or Microsoft SQL services.
The report shows a global statistics where Bangladesh has been shown at the top hit list by ransomware Trojans than any other country:

CIRT found four major ransomware incidents in 2023, including one by LockBit 3.0 targeting a top pharmaceutical company in Bangladesh. The hackers claimed to have accessed 750GB of data, including personal files of key employees, infrastructure, and accounting data.
In March 2023, a major ransomware attack occurred in Bangladesh, targeting a prominent transportation organization. The attacker, known as “Money Message,” was new to the ransomware criminal activity. The affected company’s critical server and some computers were attacked by ransomware from Money Message, causing disruption to operations. Attacker demanded a large ransom to give back access to the server and said they’d release 100GB of personal data they got into.
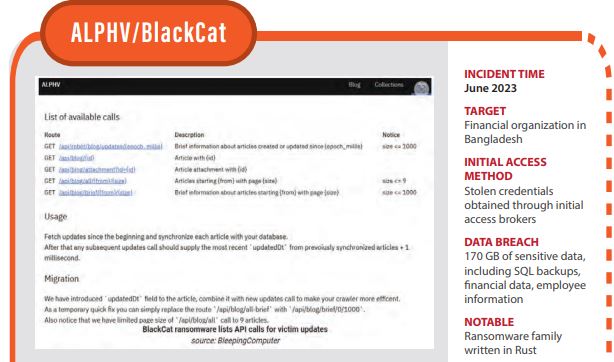
ALPHV claimed they were responsible for hacking a financial organization in Bangladesh. They were able to access 170 GB of sensitive data, including SQL backups, financial data, employee information, and more. They also claimed to have implanted a backdoor to maintain ongoing access to the network.
On June, the Akira ransomware group targeted and attacked a large company in Bangladesh. They claimed responsibility for the attack and listed the company as a victim on their website. The group stated that the company’s leadership refused to negotiate the ransom amount, so they released the company’s leaked data on their dark website.
Malware variants related to ransomware:
The CTI Unit of BGD e-GOV CIRT found different versions of ransomware threats. In the last year, they discovered 25,038 unique cases of IP addresses from Bangladesh affected by these malware infections.
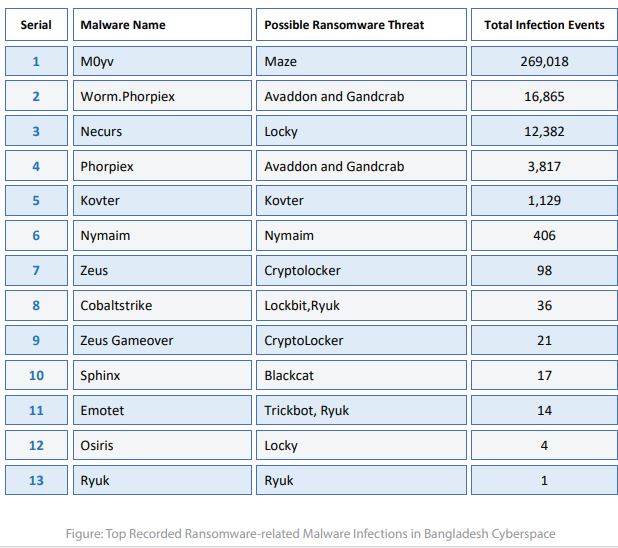
The indicators of compromise are connected to ransomware threat actors, which raises concerns about ransomware attacks on the affected networks. In 2023, there has been a significant 71.39% increase in malware infections compared to 2022, all associated with potential ransomware risks.
Active ransomware strains:
BGD e-GOV CIRT is working to identify possible ransomware activities. Its main objective is to provide useful information to protect important information systems and organizations.
In 2023, CTI unit found traces of 7 different ransomware threats. It’s important to note that none of these threats were able to infiltrate or compromise any infrastructure. However, CIRT observed active attempts from these ransomware actors. The graphic below shows these active attempts by ransomware entities:
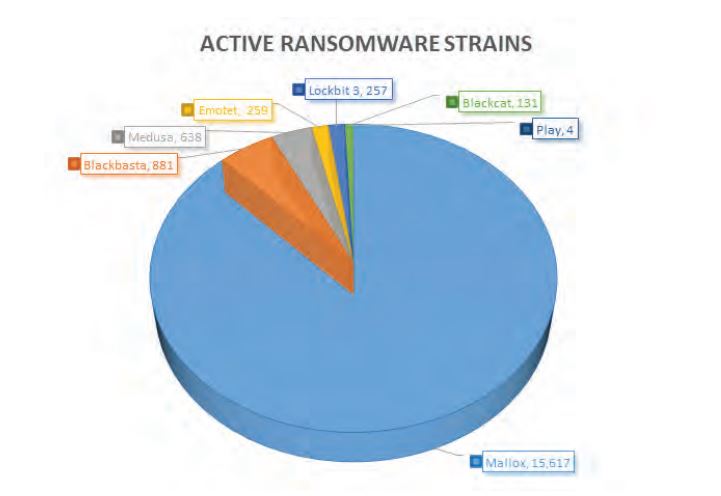
CIRT have noticed a significant increase in brute force attacks by well-known ransomware groups targeting Bangladeshi domains. Its analysis has identified traces possibly linked to the Mallox ransomware group.
This discovery is very important because it matches the warnings given by many cybersecurity companies in July of last year. They reported a huge 174% increase in Mallox ransomware activities compared to the previous year.
The Mallox group is known for attacking unsecured MS-SQL servers to get into a network. They start by trying a list of common passwords to break in, and once they’re in, they use a command line and PowerShell to download the Mallox ransomware from a remote server. Additionally, we’ve also noticed active attempts to break into etworks by other well-known ransomware threats like Blackbasta, Medusa, Emotet Lockbit 3, Blackcat, and Play.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind















