vpnMentor’s Research Team is monitoring the potential TikTok ban in the U.S., driven by national security and data privacy issues. ByteDance, TikTok’s Chinese parent company, is under pressure to sell its U.S. operations by January 19, 2025, or face a ban due to concerns about user data security and possible …
Read More »MITRE Launches D3FEND 1.0; The Milestone for Cybersecurity Ontology
MITRE launched D3FENDTM 1.0, a cybersecurity framework that provides a vocabulary and understanding of the cyber domain. D3FEND 1.0, funded by the NSA and the U.S. Department of Defense, offers a flexible and user-friendly framework for cybersecurity operations and strategic decision-making. D3FEND was initially released as a beta in June …
Read More »AWS Patches Multiple Vulns in WorkSpaces, AppStream 2.0
Amazon Web Services (AWS) has recently fixed two major security vulnerabilities in its cloud services: Amazon WorkSpaces, Amazon AppStream 2.0, and Amazon DCV (Desktop Cloud Visualization). Vulnerabilities CVE-2025-0500 and CVE-2025-0501 could let attackers conduct man-in-the-middle attacks and access remote sessions without permission. CVE-2025-0500 impacts certain versions of Amazon WorkSpaces native …
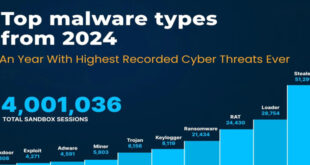
Read More »Malware Trends Review 2024: Ever Recorded Cyber Threats
Last year saw a significant rise in cyber threats, with malware becoming more advanced and attack strategies more sophisticated. A report by ANY.RUN, an interactive malware analysis platform, noted that 2024 experienced the highest levels of complex malware threats in the global cybersecurity landscape. Surge in Malware Activity: In 2024, …
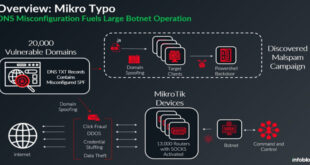
Read More »Botnet Exploits 13,000 MikroTik Devices Abusing Misconfigured DNS
A recent Infoblox Threat Intel report reveals a sophisticated botnet that exploits DNS misconfigurations to spread malware widely. This botnet, made up of about 13,000 compromised MikroTik devices, uses fake sender domains and malicious emails to deliver trojan malware and engage in other harmful activities. According to the report, “This …
Read More »
CVE-2024-9042
Code Execution Vulnerability Found in Kubernetes Windows Nodes
A new security flaw traced, CVE-2024-9042, poses a serious risk to Kubernetes clusters with Windows worker nodes. It has a Medium rating and a CVSS v3.1 score of 5.9, allowing attackers to execute commands on the host machine through the node’s /logs endpoint. A vulnerability in the Kubelet component of …
Read More »Hacker leaked 15k config files and VPN passwords of FortiGate firewall device
The hacking group “Belsen Group” has posted over 15,000 unique FortiGate firewall configurations online. The data dump, reportedly obtained by exploiting a zero-day vulnerability in Fortinet’s systems in October 2022, contains sensitive information including usernames, passwords (some in plain text), device management certificates, and complete firewall rules. “At the beginning of …
Read More »Registration open for 1st Agile Cyber Drill 2025
Registration open for “1st Agile Cyber Drill-2025” scheduled for February 26, 2025 online with an awards ceremony for 9 March an initiative by AGS Quality Action Ltd. The drill will involve companies, microfinance institutions, IT service providers, and others to evaluate their readiness for cyber risks. The drill targets corporate …
Read More »30 Days to Go for FutureCrime Summit 2025
The FutureCrime Summit 2025 is just 30 days away. This conference is the largest on technology-driven crime, covering topics like digital forensics, cybercrime, and technology laws. Grant Thornton Bharat, a leader in fraud risk management and cybersecurity, is partnering with the FutureCrime Summit 2025 to strengthen efforts against emerging cyber …
Read More »Microsoft January 2025 Patch, 159 Vuls, 10 Critical RCE’s
Microsoft’s January Patch Tuesday update fixed 159 vulnerabilities, including 10 critical Remote Code Execution (RCE) issues. These updates are essential for protecting Windows and related software from exploitation. Key Highlights of December 2024 Patch Tuesday Updates: CVE-2025-21362 & CVE-2025-21354: Both issues are vulnerabilities in Microsoft Excel that allow remote code …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind