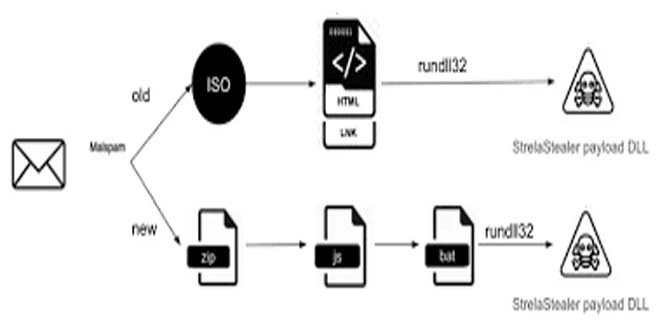
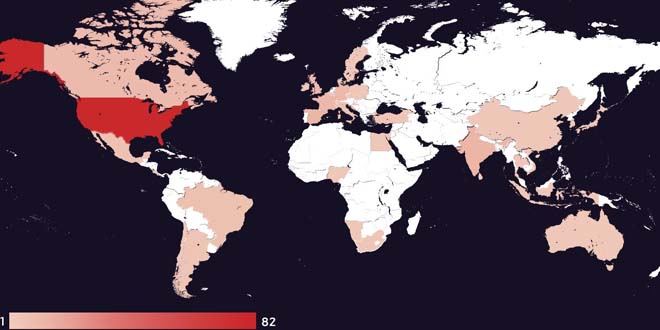
StrelaStealer malware steals email login data from popular email clients and sends it to the attacker’s server. The attacker can then use this information to launch more attacks. Since its first appearance in 2022, the threat actor has carried out many email campaigns and shows no sign of stopping.
Unit42 researchers have found a wave of big StrelaStealer campaigns affecting more than 100 organizations in the EU and U.S. These campaigns involve spam emails with attachments that activate the StrelaStealer’s DLL payload.
By infosecbulletin
/ Wednesday , May 15 2024
FBI has seized hacking forum "BreachForums" popularly known as a Breached hacking forum in the underground market on Wednesday morning...
Read More
By infosecbulletin
/ Wednesday , May 15 2024
Antivirus manufacturer Kaspersky inform that it has detected over 34,000 ransomware attacks targeting various organizations in Bangladesh from January to...
Read More
By infosecbulletin
/ Wednesday , May 15 2024
A vulnerability has been discovered in Fortinet’s FortiOS SSL-VPN and FortiProxy SSL-VPN. The flaw is identified as FG-23-225 which allows...
Read More
By infosecbulletin
/ Wednesday , May 15 2024
According to the Threatmon advanced threat monitoring platform, LockBit is in the top position in the category of top active...
Read More
By infosecbulletin
/ Wednesday , May 15 2024
On Tuesday (May 14), CISA released four Industrial Control Systems (ICS) advisories which provide timely information about current security issues,...
Read More
By infosecbulletin
/ Wednesday , May 15 2024
Microsoft patched May 2024 Tuesday including updates for 61 flaws and three publicly disclosed zero days. This update fixed Microsoft...
Read More
By infosecbulletin
/ Tuesday , May 14 2024
On Tuesday (14.05.2024) Bangladesh Bank spokesperson Majbaul Haque said to media that the information published in the report is completely...
Read More
By infosecbulletin
/ Monday , May 13 2024
The banking industry in Bangladesh is the core driver in economic development of the country. The focus on inclusion and...
Read More
By infosecbulletin
/ Monday , May 13 2024
Fortinet reported that in the second half of 2023, the average time form the disclosure of a vulnerability to its...
Read More
By infosecbulletin
/ Sunday , May 12 2024
Indian government websites have been used by scammers to place ads that send visitors to online betting sites. TechCrunch found...
Read More
Attackers change email attachment file formats to evade detection. This prevents detection from previously generated signatures or patterns. The malware author frequently updates the DLL payload with improved obfuscation and anti-analysis techniques. This makes analysis more difficult for analysts and security products.
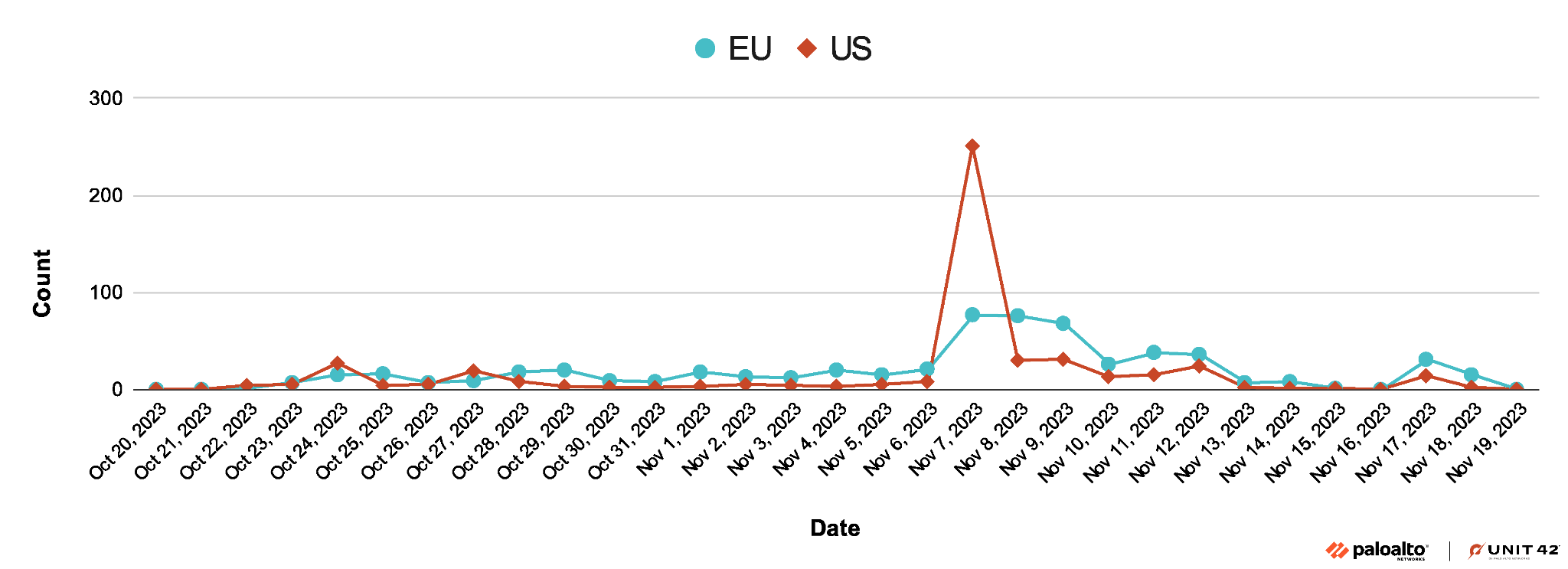
Last Large-Scale Campaign of 2023:
StrelaStealer has been causing multiple large-scale campaigns. The most recent campaign in November 2023 targeted organizations in the U.S. and EU. Figure 1 shows the timeline of this campaign.
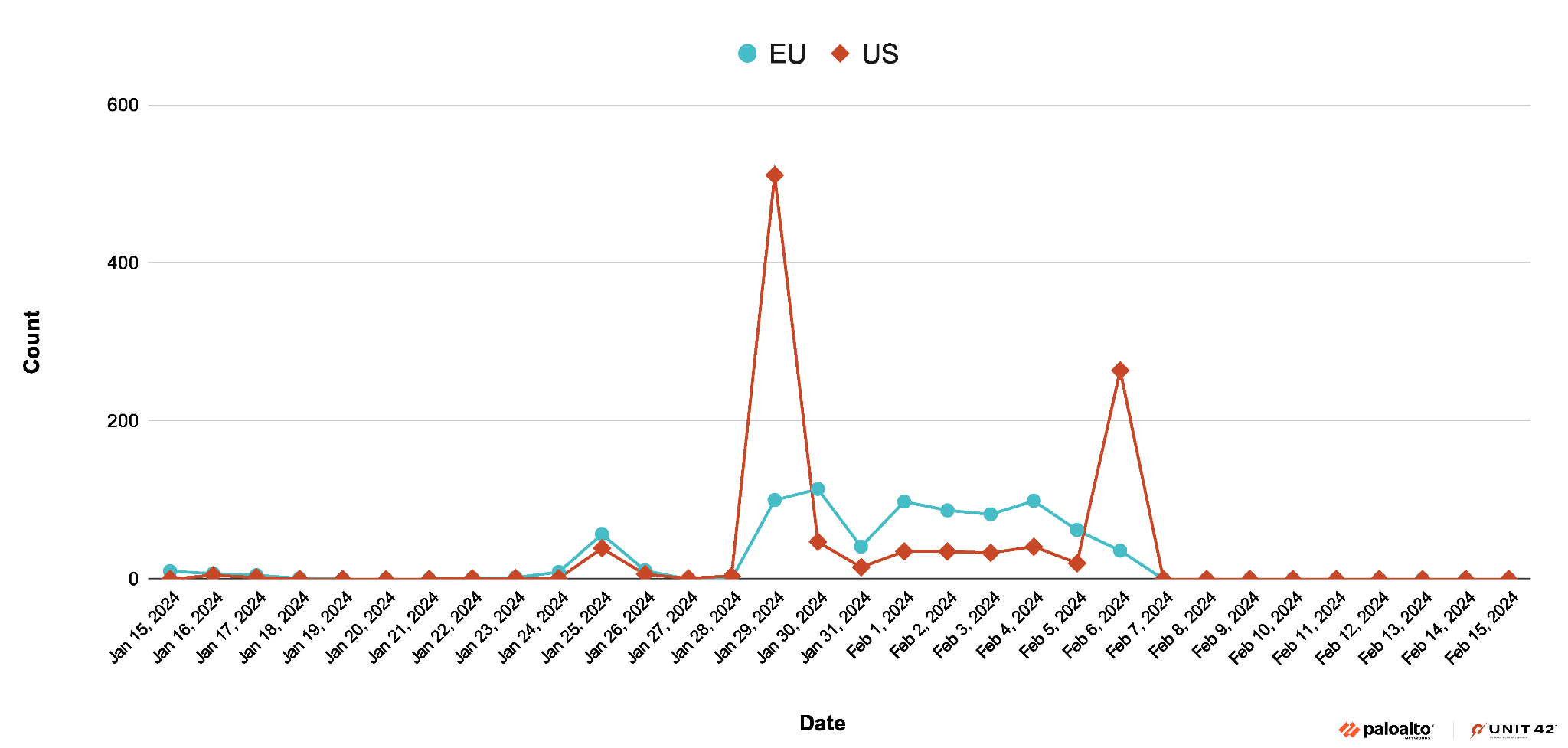
Recent Large-Scale Campaign in 2024
In January 2024, the StrelaStealer threat actors started a big campaign targeting organizations in the same areas as before. The campaign peaked on Jan. 29, 2024.
The language of the StrelaStealer spam email seen during this campaign is localized and the subject line has the pattern of Factura/Rechnung/invoice####. Figure 3, below, is a sample email in German.
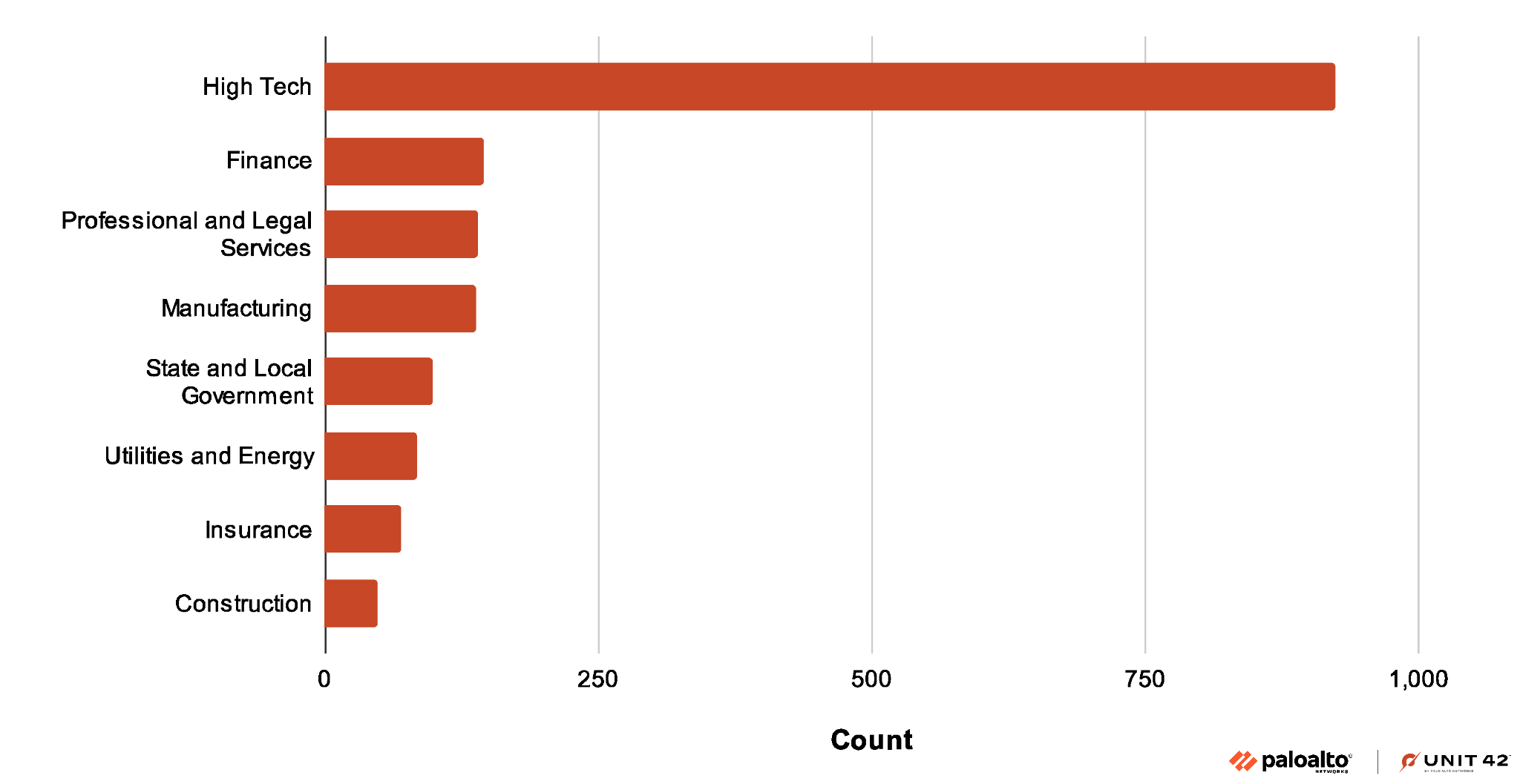
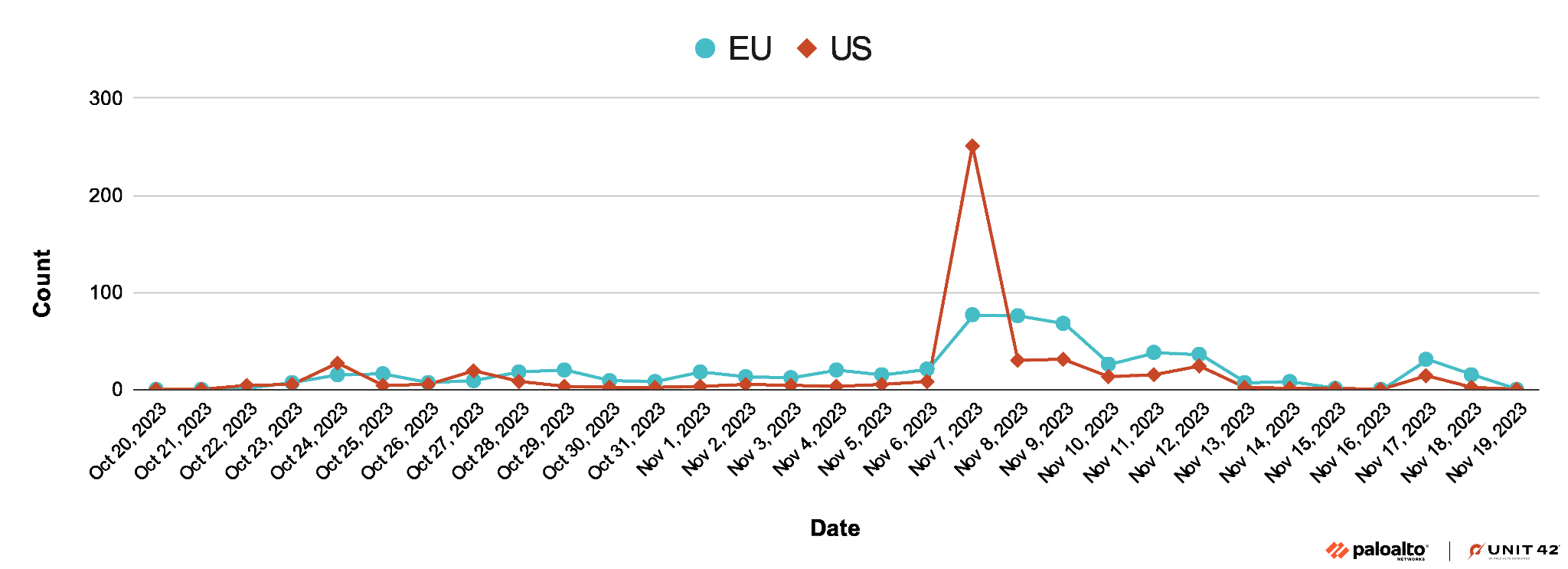 Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
For the technical analysis click here.


 Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind