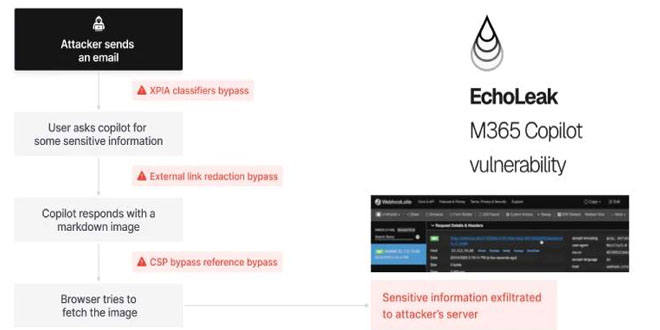
A new report from Bitsight reveals that over 40,000 internet-connected security cameras around the world are exposed, broadcasting live footage without user consent or basic security.
“Most times, all that an attacker needs to spy on homes or even large organizations is just a web browser and the right IP address,” the report warns.
By using Groma internet scanning, Bitsight uncovered live camera feeds from businesses, homes, and transport. The devices were exposed in over 100 countries, mainly in the U.S. (~14k) and Japan (~7k).
Many of these devices were from popular brands and had easy plug-and-play features, but they sacrificed cybersecurity for convenience.
“An open camera means zero privacy. Whether it’s a baby monitor, a home security camera, or a pet cam, someone out there could be watching and you’d have no idea,” the report warns.
The report showcases the dangerous ubiquity of these exposed cameras:
Homes and residential areas, where attackers can monitor family routines.
Retail stores, revealing cash registers and safe locations.
Factories, exposing proprietary manufacturing processes.
Data centers, risking exposure of sensitive infrastructure.
Hospital rooms, where even patient beds were caught on live footage.
One particularly alarming discovery: a camera monitoring an ATM, where “fraudsters would not even need to install their own hidden camera” to capture users’ PINs.
Bitsight’s researchers used non-intrusive methods to access screenshots through familiar endpoints like /out.jpg and typical RTSP paths like /live.sdp and /video.h264.
“Et voilà! Even though the camera seemed to be protected, hitting the right URI allowed us to fetch a live screenshot from the device with no authentication required,” the report notes.
The security flaws not only invade privacy but can also turn devices into botnets, like in the Mirai and Eleven11bot cases, or lead to cyberattacks such as the Akira ransomware group exploiting unsecured cameras.
The dark web features many conversations about exposed cameras. Bitsight’s cyber threat intelligence team found that attackers are scanning for these devices and sometimes leave behind taunting messages to show off on forums.
Bitsight recommends immediate action:
Disable remote access unless required.
Change default credentials immediately.
Place cameras behind firewalls or VPNs.
Update firmware regularly.
Use detection tools like Bitsight’s Open Ports risk vector to monitor for exposure.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind