Akira ransomware first appeared in 2017. It targeted video folders and encrypted the files without leaving any ransom notes. The encrypted files had the extension “.akira”.
Researchers have been working on decrypting the files affected by Akira ransomware, and they have finally made a breakthrough. Researchers at Avast have found a way to decrypt the files affected by the ransomware. Avast has also released 64-bit and 32-bit versions of the decryptor tool for users.
The decryptor tool works by reverse engineering the ransomware’s encryption algorithm. This allows the tool to decrypt files that have been encrypted by the ransomware, even if the victim does not have the ransom key.
Akira ransomware is a Windows-specific ransomware that uses 64-bit Windows binaries to encrypt files. It is written in C++ and uses a variety of C++ libraries.
The ransomware uses symmetric encryption, which means that the same key is used to encrypt and decrypt files. The encryption key is generated by the CryptGenRandom() function in Windows CryptAPI, and then used by ChaCha 2008 to encrypt files on the affected systems.
In addition to Windows, Akira ransomware has also been known to affect Linux systems. In these cases, the ransomware uses the Crypto++ library as a replacement for Windows CryptAPI.
Akira ransomware has been known to target a variety of organizations, including those in education, finance, and real estate. The ransomware typically encrypts files and demands a ransom payment in exchange for the decryption key.
By default, the ransomware excludes certain folders and file extensions from encrypting, which includes,
Files
- .exe
- .dll
- .lnk
- .sys
- .msi
- Akira_readme.txt
Folders
- winnt (default installation folder of Windows 2000)
- temp
- thumb
- $Recycle.bin
- $RECYCLE.BIN
- System Volume Information
- Boot
- Windows
- Trend Micro
How to use the Avast decryption tool to decrypt files encrypted by the ransomware
Step by step process to decrypt the file encrypted by akira ransomware:
-
- The first step is to download the decryptor binary. Avast provides a 64-bit decryptor, as the ransomware is also a 64-bit and can’t run on 32-bit Windows. If you have no choice but to use 32-bit applications, you may download 32-bit decryptor here.
- Run the executable file, preferably as an administrator. It starts as a wizard, leading you through the configuration of the decryption process.
- On the initial page, we have a link to the license information. Click the Next button when you are ready to start.
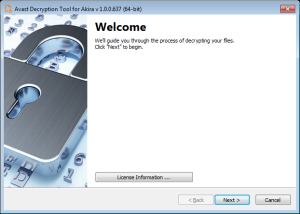
- On the next page, select the list of locations you want to be searched for and decrypted. By default, it has a list of all local drives:
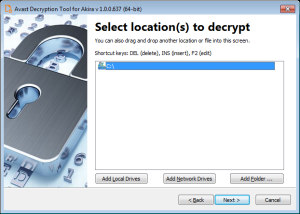
- On the following page, you need to supply an example of a file in its original form and then one encrypted by Akira ransomware. Type both names of the files. You can also drag & drop files from Windows Explorer to the wizard page.
It is extremely important to pick a pair of files that are as big as you can find. Due to Akira’s block size calculation; there may be dramatic difference on the size limit even for files that differ by a size of 1 byte.
When you click Next, the decryption tool will carefully examine the file pair and tells you what the biggest decryptable file is. In general, the size limit should be the same as the size of the original file:
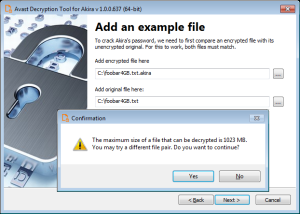
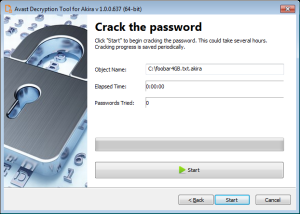
- The next page is where the password cracking process takes place. Click Start when you are ready to begin. This process usually only takes a few seconds but will require a large amount of system memory. This is why we strongly recommend using the 64-bit version of the decryption tool.
Once the password is found, you can continue to decrypt all the encrypted files on your PC by clicking Next.
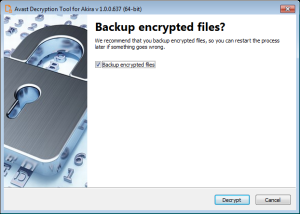
- On the final page, you can opt-in to back up your encrypted files. These backups may help if anything goes wrong during the decryption process. This choice is selected by default, which we recommend. After clicking Decrypt the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
IOCs (indicators of compromise)
Windows versions
3c92bfc71004340ebc00146ced294bc94f49f6a5e212016ac05e7d10fcb3312c
5c62626731856fb5e669473b39ac3deb0052b32981863f8cf697ae01c80512e5
678ec8734367c7547794a604cc65e74a0f42320d85a6dce20c214e3b4536bb33
7b295a10d54c870d59fab3a83a8b983282f6250a0be9df581334eb93d53f3488
8631ac37f605daacf47095955837ec5abbd5e98c540ffd58bb9bf873b1685a50
1b6af2fbbc636180dd7bae825486ccc45e42aefbb304d5f83fafca4d637c13cc
9ca333b2e88ab35f608e447b0e3b821a6e04c4b0c76545177890fb16adcab163
d0510e1d89640c9650782e882fe3b9afba00303b126ec38fdc5f1c1484341959
6cadab96185dbe6f3a7b95cf2f97d6ac395785607baa6ed7bf363deeb59cc360
Linux version
1d3b5c650533d13c81e325972a912e3ff8776e36e18bca966dae50735f8ab296
Source: Decoded avast.io, gbhacker
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind