Zyxel Networks has issued critical security patches for two high-severity vulnerabilities in its USG FLEX H series firewalls. These flaws could let attackers gain unauthorized access and escalate their privileges on the devices.
On April 22, 2025, a security advisory was released outlining patches for CVE-2025-1731 and CVE-2025-1732, affecting various firmware versions of the company’s security appliances.
Zyxel USG FLEX H Series Vulnerabilities:
Security researchers found a vulnerability (CVE-2025-1731) in the PostgreSQL commands of USG FLEX H series uOS firmware versions V1.20 to V1.31 due to incorrect permission assignments.
This critical flaw has a CVSS score of 7.8, highlighting its serious security threat. It may allow a low-privileged, authenticated local attacker to access the Linux shell and elevate their privileges to the administrator level.
The advisory explains that ” the exploitation path is particularly concerning as it enables attackers to craft malicious scripts or modify system configurations through a stolen token. “
“However, modification of system configurations is only possible if the administrator remains logged in and their token remains valid.”
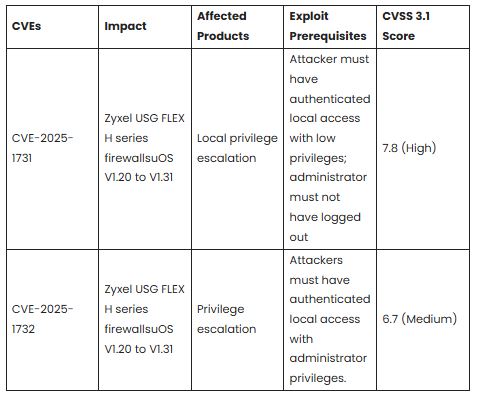
The second vulnerability, CVE-2025-1732, relates to improper privilege management in the recovery function of the same firmware versions.
This vulnerability allows an authenticated local attacker with admin privileges to upload a specially crafted configuration file, potentially escalating their privileges on affected devices.
Security researchers Alessandro Sgreccia from HackerHood and Marco Ivaldi from HN Security discovered the vulnerabilities.
Affected Systems and Patch Released:
Zyxel’s investigation found that only the USG FLEX H series is vulnerable during the current support period. They have released firmware update uOS V1.32 to fix these vulnerabilities.
Security experts advise prompt patching due to the frequent exploitation of privilege escalation vulnerabilities in targeted enterprise attacks.
The USG FLEX H series is Zyxel’s advanced security solution, offering three times the performance in firewall, VPN, and Unified Threat Management compared to earlier models, thanks to its next-generation multi-core hardware.
Users should promptly install the patches and adopt defense-in-depth strategies, such as reducing external management interface exposure and enforcing strong authentication policies.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind