Cybercriminals have increased the sale of new or stolen Gold checkmarked accounts from the X/Twitter platform. These accounts are being used by threat actors to share links to malware on the social media site, making it appear as a post from a trusted source.
Researchers at CloudSEK in Singapore have found a surge in dark web posts selling verified X/Twitter Gold accounts. Similar advertisements were also observed on the Telegram messaging site.
On Twitter, users can buy Gold, Blue, and Grey tickmarks for a monthly fee to boost their brand’s credibility. Grey checkmarks are specifically reserved for NGOs and government bodies.
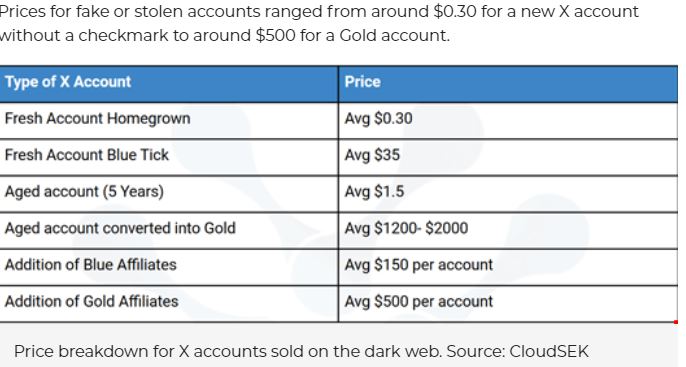
Gold accounts sold on the dark web can be used by threat actors to impersonate companies or individuals. Some are new and can be renamed, while others have been taken over by brute-force login attacks.
Prices range from an average of 30 cents for a new account to $2,000 for an aged account converted into Gold (all prices in U.S. currency). Prices go up depending on the number of followers of an existing and stolen account.
The sale on the dark web of Gold accounts has been going on since last March. CloudSEK says the number of shops and service providers today offering them “is humongous.” Most can be detected by running simple Google Dork queries.
Researchers are concerned that the increase in Gold accounts available on the dark web may lead to a surge in phishing and disinformation attacks. Usually buyers have access to an account for 30 days, which is the standard duration of X/Twitter Gold subscriptions.
Hackers often target X/Twitter accounts belonging to organizations that were created before 2022 and have not been used or abandoned. They attempt to gain access to the account by using brute force methods. If they are successful, they change the recovery email and contact details, preventing the original owner from regaining control. These compromised accounts are then sold as “Gold” based on the demand from buyers.
Hackers use a tactic to collect Twitter logins from information stealer malware. They check the logins using configs and brute force methods to find working accounts. Then, they sell these accounts on hacker forums as “Twitter Gold” for as little as US$800.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind