Security researchers found that three unauthorized TLS certificates were issued in May 2025 for 1.1.1.1, the public DNS service operated by Cloudflare.
Improperly issued certificates by the Fina RDC 2020 authority could let attackers intercept and decrypt DNS queries, revealing users’ browsing habits.
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
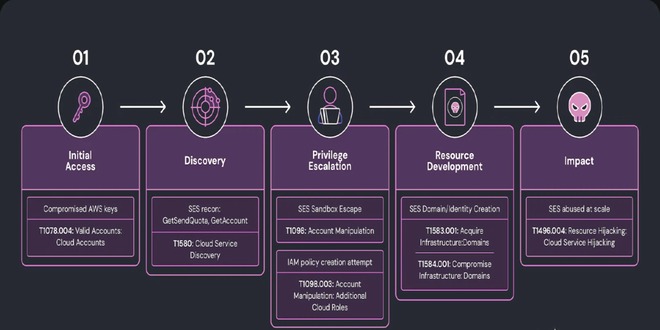
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
By infosecbulletin
/ Sunday , September 7 2025
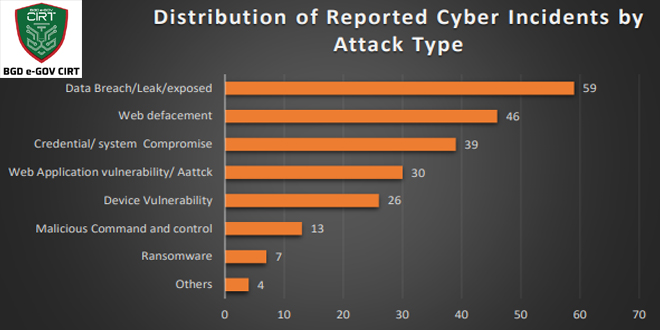
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year...
Read More
By infosecbulletin
/ Sunday , September 7 2025
Investigations into the Nx "s1ngularity" NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and...
Read More
By infosecbulletin
/ Saturday , September 6 2025
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR)...
Read More
However, if a malicious or unauthorized party holds a valid certificate, they can impersonate the domain and carry out what is known as an “adversary-in-the-middle” attack.
Fina RDC 2020 certificates were automatically trusted on Windows and Microsoft Edge because they are linked to the Fina Root CA.
The root certificate belongs to Microsoft’s Root Certificate Program. Major browsers like Google Chrome and Mozilla Firefox, along with Apple’s Safari, do not trust Fina. Therefore, only users of Windows and Edge were at risk.
Cloudflare confirmed that it did not request or authorize the issuance of these certificates. “Upon seeing the report on the certificate-transparency email list, we immediately kicked off an investigation and reached out to Fina, Microsoft, and Fina’s TSP supervisory body,” said a Cloudflare spokesperson.
“These parties can mitigate the issue by revoking the trust in Fina or revoking the mis-issued certificates. We also want to reassure users that our WARP VPN service was not affected.”
Microsoft indicated it has already “engaged the certificate authority to request immediate action” and plans to block the rogue certificates by adding them to its disallowed certificate list.
The company did not explain how the certificates evaded detection for four months, despite their creation in May.
This situation shows a serious flaw in the internet’s certificate system, where the failure of one certificate authority can affect the trust that millions depend upon.
Hacker accessed Brazil’s Real-Time Payment System: Attempted grabing $130M
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind