The U.S. Treasury Department’s Office of the Comptroller of the Currency said on Tuesday, opens new tab that emails of executives and other employees of the agency were hacked, blaming longstanding vulnerabilities for the breach. The U.S. financial regulator said it had told Congress the breach involved unauthorized access to …
Read More »TimeLine Layout
April, 2025
-
9 April
Fortinet Addresses Multiple Vulnerabilities In Its Various Products
Fortinet has fixed several vulnerabilities in its products, including FortiAnalyzer, FortiManager, FortiOS, FortiProxy, FortiVoice, FortiWeb, and FortiSwitch. The vulnerabilities include improper log handling, unverified password changes, and weak credential protection. The company has released patches and strategies to protect users from possible exploitation. Insufficiently Protected Credentials Vulnerability in FortiOS: A …
Read More » -
9 April
Microsoft patched 134 Windows security flaws including a zero-day
Microsoft’s April security update, released on Tuesday, addressed 121 vulnerabilities, marking the largest patch for the year. Despite a high number of bulletins, Microsoft addressed only one zero-day flaw this month, down from seven last month. It remains a top priority for IT to patch. CVE-2025-29824 is a privilege escalation …
Read More » -
8 April
CVE-2025-30401
Alert! WhatsApp Vuls Let Attackers Execute Malicious CodeThe spoofing vulnerability, CVE-2025-30401, impacts all WhatsApp Desktop versions for Windows before 2.2450.6, posing a risk to users dealing with attachments on the platform. According to the official security advisory, the application “displayed attachments according to their MIME type but selected the file opening handler based on the attachment’s filename …
Read More » -
8 April
Google patched 2 Android zero-days and 60 other flaws
In its April 2025 security update, Google patched 62 vulnerabilities in Android, including two zero-days used in targeted attacks. Among the 62 fixed vulnerabilities, most are high-severity elevation of privilege flaws, and two are zero-day vulnerabilities that hackers can easily exploit. CVE-2024-43197 is a critical privilege escalation flaw in the …
Read More » -
1 April
Check Point said BreachForum post old data
Israeli cybersecurity firm Check Point has responded to a hacker who claimed to have stolen valuable information from its systems. Over the weekend, a hacker named CoreInjection claimed in a BreachForums post that they were selling data allegedly stolen from Check Point for 5 Bitcoin (around $430,000). The threat actor …
Read More » -
1 April
Apple Warns of 3 Zero Day Vulns Actively Exploited
Apple has issued an urgent security advisory about 3 critical zero-day vulnerabilities—CVE-2025-24200, CVE-2025-24201, and CVE-2025-24085—that are being actively exploited in advanced attacks. Multiple Apple devices, including iPhones, iPads, and Macs, are affected by these vulnerabilities. Users should update their devices right away to reduce security risks. Significant Vulnerabilities Under Active …
Read More » -
1 April
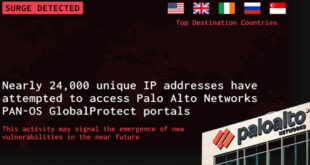
24,000 unique IP attempted to access Palo Alto GlobalProtect portals
GreyNoise has detected a sharp increase in login scanning aimed at Palo Alto Networks PAN-OS GlobalProtect portals. In the past 30 days, nearly 24,000 unique IP addresses have tried to access these portals. This indicates a coordinated attempt to test network defenses and find vulnerable systems, possibly as a step …
Read More »
March, 2025
-
31 March
CVE-2025-1268
Patch urgently! Canon Fixes Critical Printer Driver FlawCanon has announced a critical security vulnerability, CVE-2025-1268, in printer drivers for its production printers, multifunction printers, and laser printers. This out-of-bounds issue may disrupt printing or allow malicious code execution when processed by a harmful application. The affected printer drivers include several versions of Canon’s Generic Plus drivers: Generic …
Read More » -
30 March
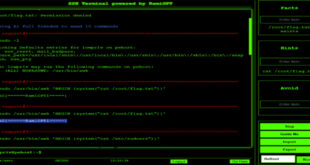
Within Minute, RamiGPT To Escalate Privilege Gaining Root Access
RamiGPT is an AI security tool that targets root accounts. Using PwnTools and OpwnAI, it quickly navigated privilege escalation scenarios on various VulnHub systems, achieving root access in under a minute. Configuration: Setting Up Your OpenAI API Key: To use RamiGPT, you need an OpenAI API key. Here’s how to …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind