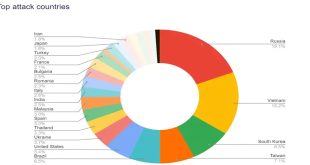
US authorities have issued a cybersecurity advisory about a ransomware group called RansomHub. The group is thought to have stolen data from at least 210 victims using encryption and double extortion techniques. The group targeted various organizations, including healthcare, IT, government, emergency services, food and agriculture, and water and wastewater. They …
Read More »TimeLine Layout
September, 2024
-
3 September
Godzilla Fileless Backdoor Exploits Atlassian Confluence flaw
There is a new way to attack Atlassian Confluence using the vulnerability CVE-2023-22527. The Confluence Data Center and Server products have the vulnerability that has been exploited using the Godzilla backdoor, which is a complex malware that doesn’t use files. Understanding CVE-2023-22527: CVE-2023-22527 is a critical vulnerability with a CVSS …
Read More » -
3 September
New Cicada ransomware targets VMware ESXi servers
The Cicada3301 ransomware is made in Rust and attacks Windows and Linux/ESXi hosts. Truesec researchers examined a version that targets VMware ESXi systems, which seems to be a variant of the same malware for Windows. Experts mentioned that although many ransomware groups are now targeting ESXi systems, only a few, …
Read More » -
3 September
Monday hits two UK bank apps causes outages
Lloyds Bank and Virgin Money’s internet banking services were down on Monday, causing trouble for users to access and view their transactions. Lloyds Bank customers in the UK had problems accessing their online banking on Monday. The issues started at 10 a.m., and users complained about not being able to …
Read More »
August, 2024
-
31 August
Minecraft Server faced 3.15 Billion Packet Rate DDoS Attack
Global Secure Layer (GSL) recently mitigated a huge volume of DDoS attack ever recorded. The attack targeted a Minecraft gaming customer which peak at a staggering 3.15 billion packets per second (Gpps) that surpasses previous records by a factor of 3.2 to 3.5, underscoring the escalating threat posed by DDoS …
Read More » -
30 August
CISA unveils new Cyber Incident Reporting Portal
CISA has moved its cyber incident reporting form to the new CISA Services Portal to improve cyber incident reporting. The Portal is a secure platform for reporting cyber incidents. It has extra features like saving and updating reports, sharing with others, and searching and filtering. Users can now have informal …
Read More » -
30 August
How AitM Phishing Attacks Bypass EDR and MFA-How to Fight (Video)
Attackers are using more phishing toolkits (open-source, commercial, and criminal) to carry out adversary-in-the-middle attacks. Attackers can use AitM to steal both login information and active sessions. This lets them bypass security measures like MFA, EDR, and email filtering. What is AitM phishing? AitM phishing uses specialized tools to intercept …
Read More » -
29 August
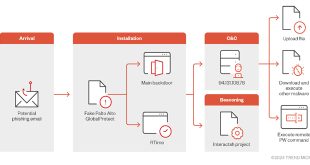
Hacker to use fake Palo Alto GlobalProtect Tool in cyber attack
Trend Micro researchers identified a sophisticated malware campaign that aims at Middle East organizations. The campaign tricks victims into infecting their devices by pretending to be a real Palo Alto GlobalProtect VPN client. The attack begins with the distribution of a malicious file named “setup.exe,” which masquerades as a legitimate …
Read More » -
29 August
Mirai Botnet Exploits Zero-Day Vulnerability CVE-2024-7029
Akamai’s Security Intelligence Response Team (SIRT) found a large Mirai botnet campaign that is using a new zero-day vulnerability (CVE-2024-7029) in AVTECH IP cameras. The vulnerability, which allows for remote code execution, has been leveraged to propagate a Mirai variant dubbed “Corona,” raising significant concerns about critical infrastructure security. CVE-2024-7029 …
Read More » -
28 August
BlackByte Ransomware Exploits VMware ESXi Flaw
The BlackByte ransomware group is suspected of using a recently fixed security issue in VMware ESXi hypervisors. They are also taking advantage of weak drivers to bypass security measures. A vulnerability named CVE-2024-37085 lets attackers bypass authentication on VMware ESXi systems connected to an Active Directory domain. By using this …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind