“A threat actor has reportedly claimed to gain root-level access to Titas Gas’s firewall server and is actively offering this access for sale on the dark web, posing a serious risk to Bangladesh’s energy infrastructure”. Bangladesh Cyber Security Intelligence (BCSI) reported that someone has reportedly gained unrestricted access to Titas …
Read More »TimeLine Layout
November, 2024
-
1 November
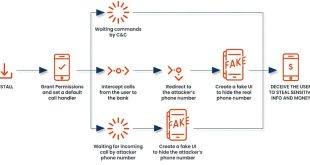
New malware FakeCall intercepts your calls to the bank
Zimperium researchers have found a new version of FakeCall malware for Android that threatens financial security. This malware redirects users’ calls to their banks to the attacker’s phone number, aiming to steal sensitive information and funds. FakeCall is a banking trojan used for voice phishing, misleading victims into giving sensitive …
Read More » -
1 November
Hikvision Patches Security Flaw in Network Cameras
Hikvision, a top provider of network cameras, has issued firmware updates to fix a security vulnerability that could reveal users’ Dynamic DNS credentials. This issue impacts various Hikvision camera models and may allow attackers to access sensitive information or disrupt camera communication with the Dynamic DNS service. The Vulnerability: Older …
Read More » -
1 November
SonicWall report
Government Sector faces 236% Surge in Malware AttacksGlobal threat actors have significantly increased attacks on government sectors, with malware-driven attempts rising by triple digits in the first quarter of the year, according to SonicWall. The security vendor’s analysis shows a 236% increase in blocked attacks in Q1 2024 compared to last year, along with a 27% rise …
Read More »
October, 2024
-
31 October
Bangladesh Kubernetes User Group Meetup successfully completed
Meetup of Bangladesh Kubernetes User Group was held at Banani Club 9294, Dhaka on Thursday, 31 October 2024. A lively and educational evening was organized with the participation of top Kubernetes experts and technology enthusiasts of the country. The meetup organized lectures and experience sharing sessions on several important topics. …
Read More » -
31 October
Bangladesh Bank issues cyber threat alert
Bangladesh Bank issues alert on cyber threat. In its alert the central bank said, according to Bangladesh cyber security intelligence (BCSI)’s observation, some banks customers are victim to unauthorized transaction through Facebook ad manager. In this situation, Bangladesh Bank notifies the banks to take precautionary action to secure the account …
Read More » -
31 October
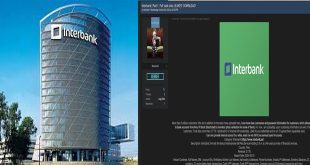
Hacker claim data breach: bank confirms blaming third party
Interbank, a major financial institution in Peru, has confirmed a data breach after a hacker leaked stolen data online. Formerly the International Bank of Peru, the company offers financial services to over 2 million customers. “To our clients: We regret this situation and understand the inconvenience this may cause you. …
Read More » -
30 October
CISA Launches Its First Ever International Strategic Plan
The US Cybersecurity and Infrastructure Security Agency (CISA) has released its first international strategic plan to enhance global cooperation in addressing cyber threats to critical infrastructure. The plan recognizes that cyber risks are complex and spread across different regions, highlighting the importance of quickly sharing threat information and risk reduction …
Read More » -
29 October
Rented bank account used to illegal transection: 5 arrested
The Indian Cyber Crime Coordination Centre (I4C) has warned about illegal payment gateways set up by transnational cyber criminals using mule bank accounts for money laundering. The Ministry of Home Affairs (MHA) reported that recent nationwide raids by the Gujarat and Andhra Pradesh Police uncovered illegal digital payment gateways created …
Read More » -
28 October
Successfully held “InfoSecCon-2024″at Dhaka Bangladesh
With a festive look and the participation of more than one hundred participants from Bangladesh cyber industry, another successful cyber security conference “InfoSecCon-2024” (2nd Edition) was held at Dhaka on 26 October (Saturday) 2nd time in a year. The very flagship event was designed with five time demanding topic including …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind