In a blog post BishopFox said, SonicWall next-generation firewall (NGFW) series 6 and 7 devices are affected by two unauthenticated denial-of-service vulnerabilities with the potential for remote code execution.
SonicWall published advisories for CVE-2022-22274 and CVE-2023-0656 a year apart and reported that no exploitation had been observed in the wild; however, a proof-of-concept exploit for the latter was publicly released.
Research found that the two issues are fundamentally the same but exploitable at different HTTP URI paths due to reuse of a vulnerable code pattern. In-depth analysis of the underlying bug allowed us to produce a test script that can determine whether a device is vulnerable without crashing it. Download it here.
Jon Williams, Senior Security Engineer at bishopfox said, using BinaryEdge source data, we scanned SonicWall firewalls with management interfaces exposed to the internet and found that 76% (178,637 of 233,984) are vulnerable to one or both issues.
according to Bishop Fox,, Although the two vulnerabilities are essentially the same as they’re caused by reusing the same vulnerable code pattern, they’re exploitable at different HTTP URI paths.
“Our initial research confirmed the vendor’s assertion that no exploit was available; however, once we identified the vulnerable code, we discovered it was the same issue announced a year later as CVE-2023-0656,” Williams said.
“We found that CVE-2022-22274 was caused by the same vulnerable code pattern in a different place, and the exploit worked against three additional URI paths.”
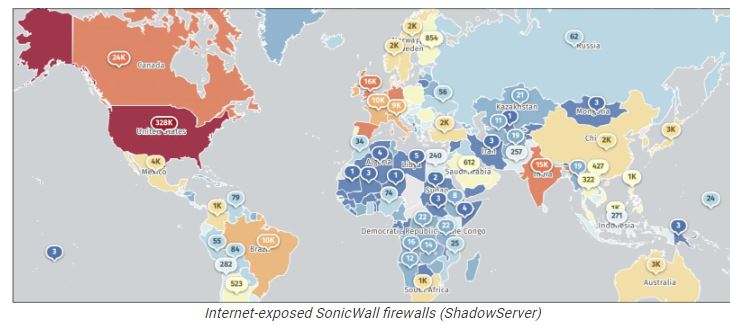
According to the data of threat monitoring platform Shadowserver, More than 500,000 SonicWall firewalls are currently exposed online, with over 328,000 in the United States.
Bleeping computer reported that the SonicWall Product Security Incident Response Team (PSIRT) says it has no knowledge that these vulnerabilities have been exploited in the wild, at least one proof-of-concept (PoC) exploit is available online for CVE-2022-22274.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind