DroidBot is a sophisticated Android Remote Access Trojan (RAT) that merges traditional hidden VNC and overlay functions with spyware-like features. It includes a keylogger and monitoring tools for intercepting user actions, making it effective for surveillance and stealing credentials.
A key feature of DroidBot is its dual-channel communication: it uses the MQTT protocol for sending data from infected devices and HTTPS for receiving commands like overlay targets, improving its flexibility and resilience.
As of the analysis, 77 different targets have been identified, including banks, cryptocurrency exchanges, and national organizations, highlighting its potential for significant impact. The threat actor behind DroidBot is linked to Turkey, indicating a trend of adapting tactics and focus areas.
Analysis of DroidBot samples uncovered its Malware-as-a-Service (MaaS) infrastructure, revealing 17 distinct affiliate groups with unique identifiers. Notably, several affiliates communicated through the same MQTT server, indicating potential collaboration or joint demonstrations of the malware’s capabilities.
DroidBot is actively being developed. Some functions, like root checks, are just placeholders and not fully implemented, while other features differ between samples, indicating ongoing improvements. Despite this, the malware has already shown its potential, successfully targeting users in the UK, Italy, France, Spain, and Portugal, with plans to expand into similar Latin American regions.
DroidBot is sophisticated and adaptable, featuring advanced surveillance, dual-channel communication, a diverse target list, and an active MaaS infrastructure. As it evolves, it increasingly threatens financial institutions, government entities, and other high-value targets globally.
“It includes a keylogger and monitoring routines that enable the interception of user interactions, making it a powerful tool for surveillance and credential theft”, the Cleafy TIR team.
TTP Behind DroidBot Campaigns:
Attackers use familiar tactics to deceive victims into downloading and installing DroidBot.
The malware disguises itself as popular banking apps, Google services, or generic security apps.
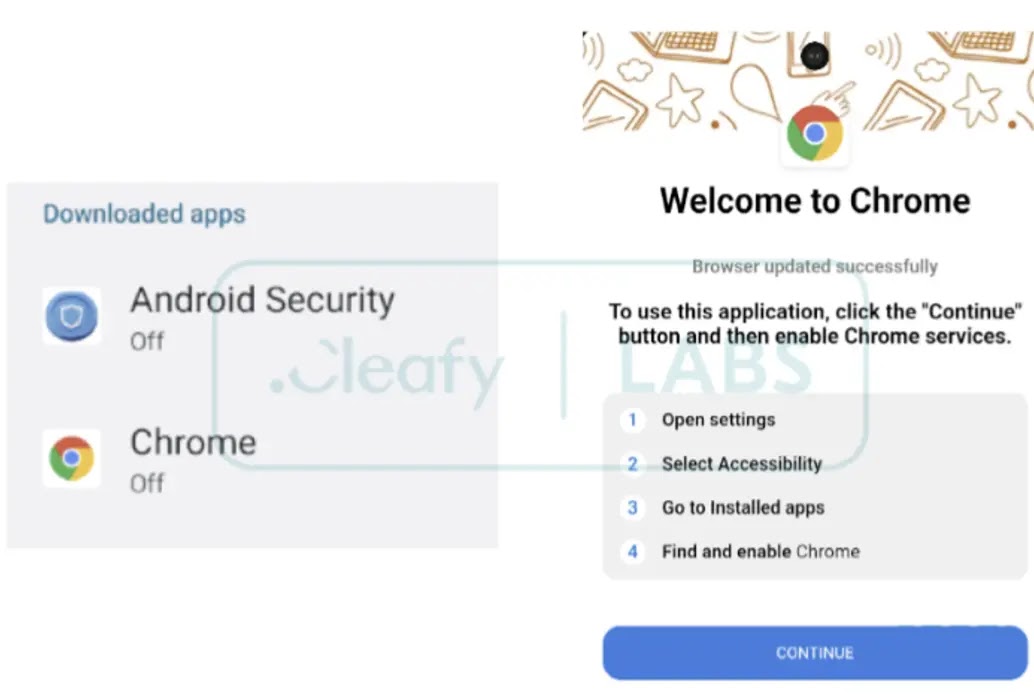
DroidBot primarily operates maliciously by exploiting Accessibility Services. It appears to have been developed using the B4A framework, commonly used for native Android apps.
B4A is often used in malware developed by Brazilian threat actors, such as the Brata family and its CopyBara variant.
click here to read out the full report.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind