LockBit restarted their ransomware operation on a new infrastructure after law enforcement disrupted their servers. Now, they threat to target the government sector more with their attacks.
The gang posted a long message admitting their negligence and sharing their future plans. “Due to my personal negligence and irresponsibility I relaxed and did not update PHP in time.” The threat actor says that the victim’s admin and chat panels server and the blog server were running PHP 8.1.2 and were likely hacked using a critical vulnerability tracked as CVE-2023-3824.
By infosecbulletin
/ Sunday , June 29 2025
Doctors at Columbia University Fertility Center have reported what they are calling the first pregnancy using a new AI system,...
Read More
By infosecbulletin
/ Saturday , June 28 2025
Cybersecurity experts and federal authorities are warning that the Scattered Spider hackers are now targeting aviation and transportation, indicating a...
Read More
By F2
/ Saturday , June 28 2025
Since June 9, 2025, Russian users connecting to Cloudflare services have faced throttling by ISPs. As the throttling is being...
Read More
By infosecbulletin
/ Saturday , June 28 2025
A new report from SafetyDetectives reveals that hackers posted a massive 3.1GB dataset online, containing about 61 million records reportedly...
Read More
By infosecbulletin
/ Friday , June 27 2025
A 30-year-old robotics engineer from Chennai set off alarm bells in 11 states by allegedly sending hoax bomb threats. She...
Read More
By infosecbulletin
/ Friday , June 27 2025
Cisco has issued updates to fix two critical security vulnerabilities in Identity Services Engine (ISE) and ISE Passive Identity Connector...
Read More
By F2
/ Thursday , June 26 2025
CISA warns about a serious vulnerability in Fortinet FortiOS that threatens network security. CISA included CVE-2019-6693 in its Known Exploited...
Read More
By F2
/ Thursday , June 26 2025
Rapid7 has revealed serious vulnerabilities in multifunction printers (MFPs) from Brother, FUJIFILM, Ricoh, and Toshiba Tec Corporation. These findings, covering...
Read More
By infosecbulletin
/ Wednesday , June 25 2025
Citrix has issued security updates for a critical vulnerability in NetScaler ADC that has been actively exploited. The vulnerability CVE-2025-6543...
Read More
By F2
/ Wednesday , June 25 2025
SonicWall warned on Monday that unknown attackers have trojanized its SSL-VPN NetExtender application, tricking users into downloading it from fake...
Read More
LockBit ransomware continues attacks:
On Saturday, the gang said it was restarting its ransomware business and acknowledged that their carelessness led to law enforcement stopping its activity in Operation Cronos.
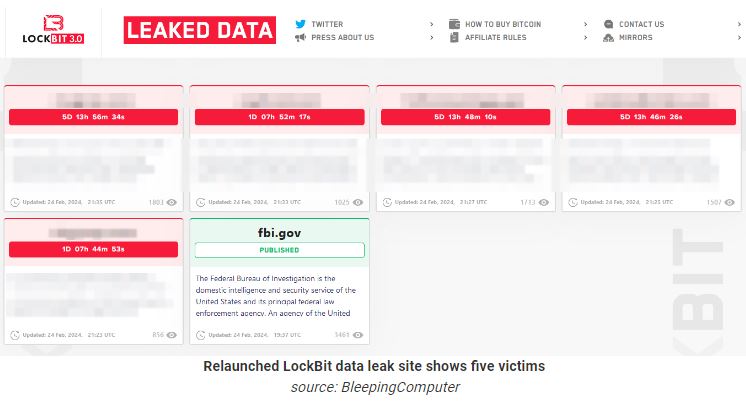
Keeping their name as usual, LockBit moved its data leak site to a new .onion address where five new victims name disclosed.
6 days back, “Operation Cronos” was led by the UK’s National Crime Agency (NCA) with support from Europol, Eurojust, and global law enforcement agencies. The task force was able to take control of 34 servers that made up LockBit’s primary platform, as well as 14,000 accounts used by the group to host tools and store data stolen from victims. The operation also seized 200 crypto-wallets and 1,000 decryption keys which were used to develop a decryptor tool that is now available to the public.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind