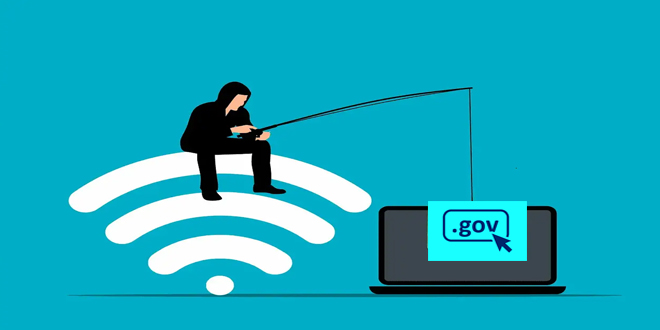
A recent report from Cofense Intelligence highlights a concerning trend: threat actors are increasingly misusing .gov top-level domains (TLDs) to execute phishing campaigns. Between November 2022 and November 2024, attackers have leveraged vulnerabilities in government websites from various countries to host malicious content, act as command-and-control (C2) servers, and funnel users to credential phishing sites.
Attackers are exploiting trust in .gov domains by using open redirect vulnerabilities, especially through CVE-2024-25608 in the Liferay digital experience platform. This allows them to evade secure email gateways and lure victims into clicking malicious links.
Attackers often exploit open redirect vulnerabilities, where a web application allows users to input a URL for redirecting them to an external site. The Cofense report states: “Threat actors regularly take advantage of open redirects such as Google AMP and TikTok to bypass secure email gateways (SEGs), and .gov domains are similarly abused.”
Threat actors use .gov URLs in phishing emails to exploit trust in government domains, tricking users into clicking links that lead to fake Microsoft login pages for credential theft.
“The campaigns abusing United States-based .gov domains for open redirects were all Microsoft-themed with the credential phishing page typically including Microsoft logos and indicators.”
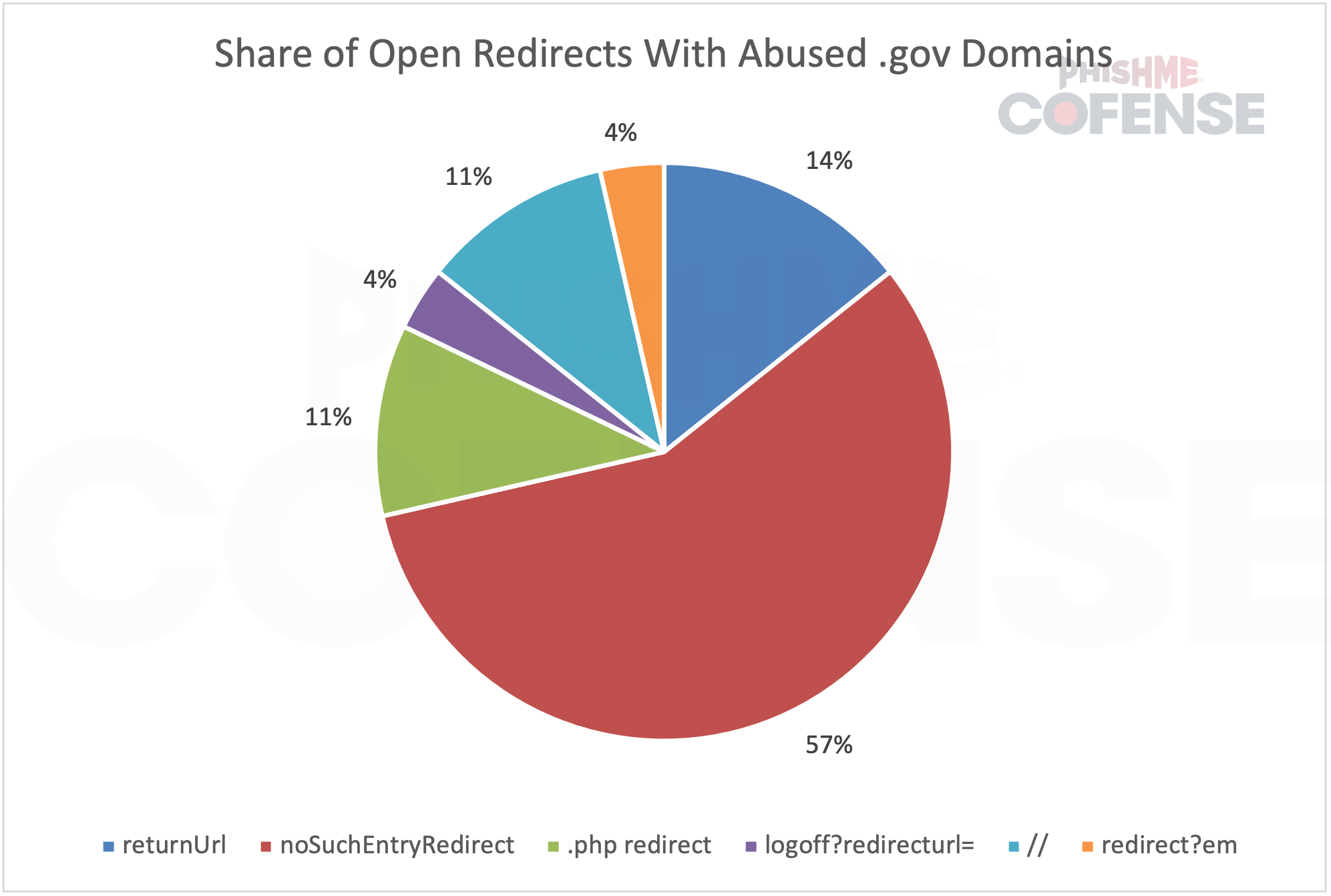
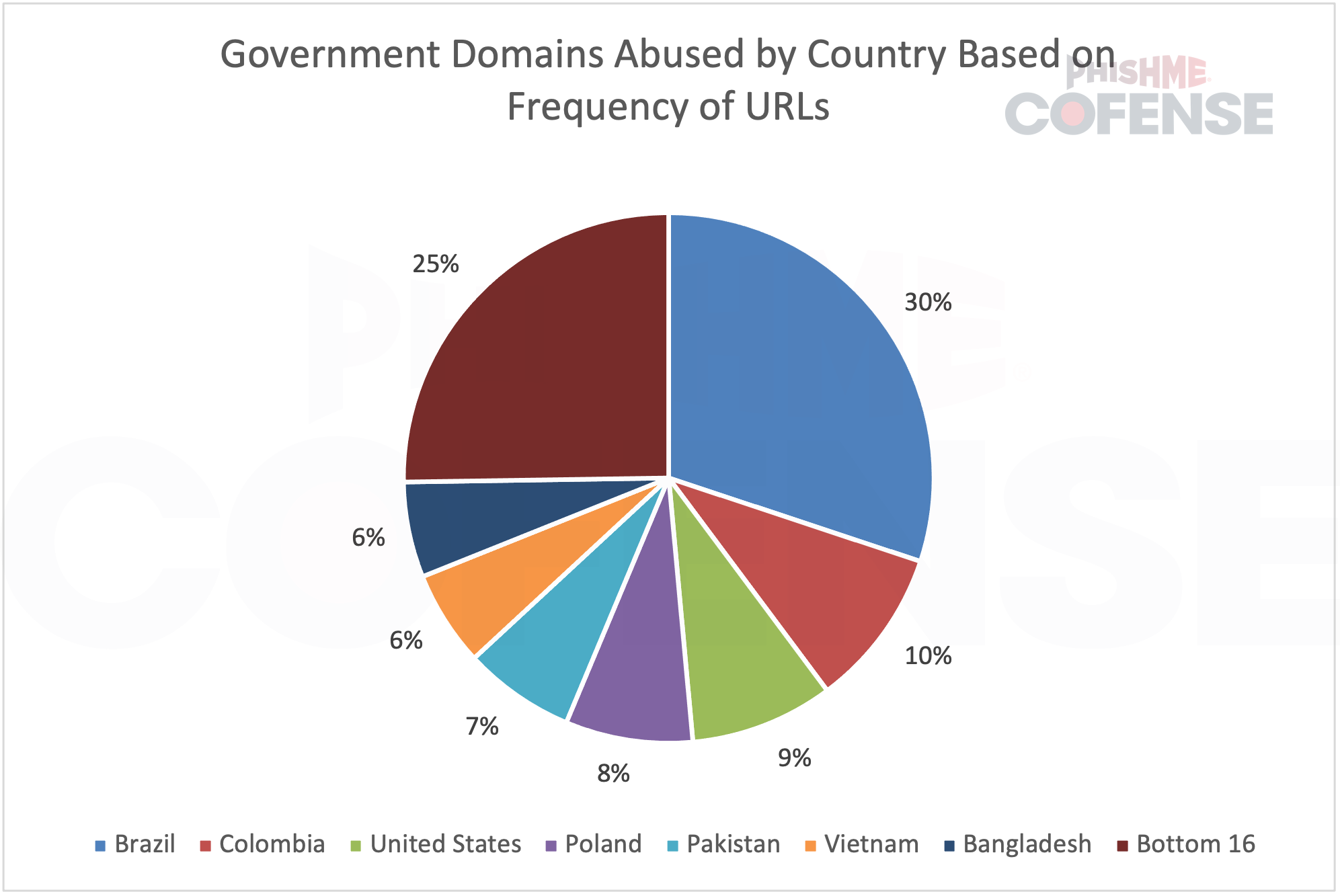
U.S. government .gov domains made up only 9% of abused domains but were still the third most exploited globally. All instances of abuse involved open redirects. The report notes that: “Over 77% of the open redirects used made use of ‘noSuchEntryRedirect,’ making it likely that the United States-based government websites also fell prey to CVE-2024-25608.”
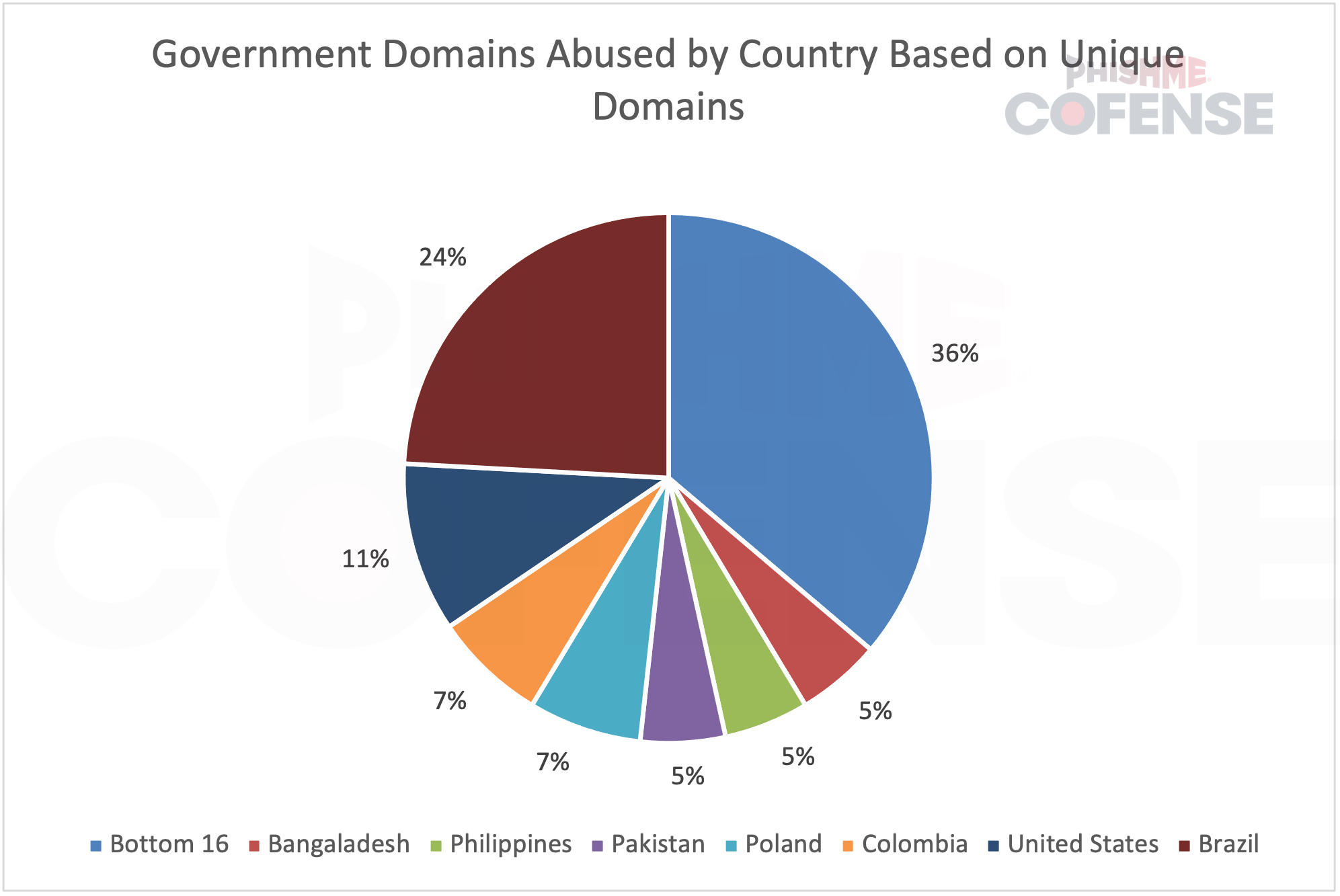
Brazil’s .gov.br domains were the most targeted globally, exceeding the combined totals of the next three countries. However, the report indicates this may be due to a few specific domains being targeted repeatedly, rather than all Brazilian government websites facing widespread attack.
The ability of .gov domains to bypass security email gateways is concerning. Major email security solutions like Microsoft ATP, Proofpoint, Cisco IronPort, Symantec MessageLabs, and Mimecast failed to filter phishing emails that misuse government open redirects.. “This is a good indicator of how successful .gov domains are at bypassing SEGs.”
Attackers often create phishing emails that appear to be about document signing or legitimate business requests. Many users trust government websites and fail to check the full URL, making them easy victims of redirection-based phishing.
Cofense Intelligence found that, in addition to phishing, some .gov domains were abused by cybercriminals using compromised government email addresses as command and control servers for malware. In mid-2023 and early 2024, these emails were used for Agent Tesla Keylogger and StormKitty malware.
The report indicates that only two government email addresses were exploited, showing that while email security in government is generally strong, it is not completely safe from attacks.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind