GitLab has released security updates for its Community Edition (CE) and Enterprise Edition (EE) to fix vulnerabilities that could enable cross-site scripting (XSS) attacks and bypass group restrictions.
CVE-2025-6948 is a critical cross-site scripting (XSS) vulnerability with a CVSS score of 8.7. It affects all versions prior to 17.11.6, 18.0.4, and 18.1.2. GitLab states that this flaw lets attackers execute actions for users by injecting harmful content, potentially compromising sessions, altering project data, or enabling phishing attacks.
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
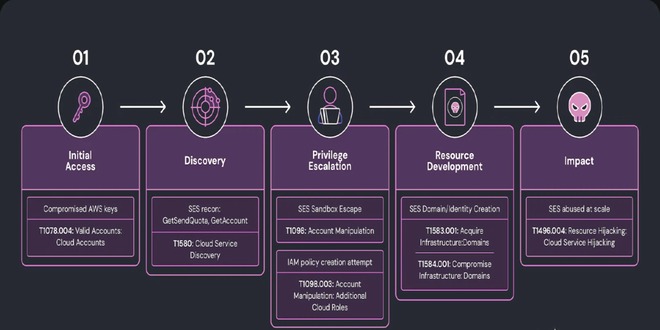
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
By infosecbulletin
/ Sunday , September 7 2025
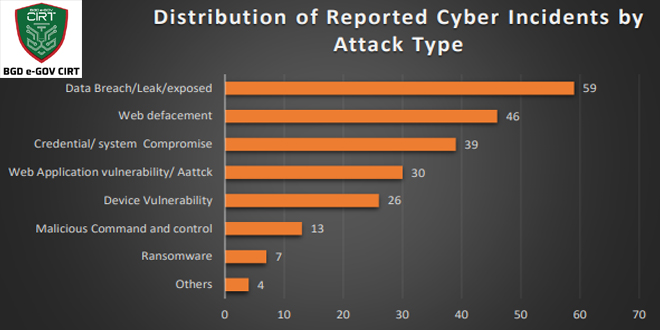
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year...
Read More
By infosecbulletin
/ Sunday , September 7 2025
Investigations into the Nx "s1ngularity" NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and...
Read More
By infosecbulletin
/ Saturday , September 6 2025
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR)...
Read More
CVE-2025-3396 is a flaw in GitLab CE/EE versions from 13.3 to 17.11.6, 18.0 to 18.0.4, and 18.1 to 18.1.2 that involves improper authorization. It has a CVSS score of 4.3 and lets authenticated project owners bypass forking restrictions by manipulating the API.
CVE-2025-4972 affects only GitLab EE and has a CVSS score of 2.7. Authenticated users with group invitation rights can bypass admin restrictions through specially crafted API requests. Affected versions are 18.0 prior to 18.0.4 and 18.1 prior to 18.1.2.
The new vulnerability in GitLab EE, CVE-2025-6168, affects versions 18.0 before 18.0.4 and 18.1 before 18.1.2, with a CVSS score of 2.7. It allows maintainers to invite users to restricted groups through special API requests, bypassing admin controls.
GitLab has upgraded its rsync utility to version 3.4.1 to fix vulnerabilities CVE-2024-12084 and CVE-2024-12088. They advise all self-managed GitLab administrators to update to versions 18.1.2, 18.0.4, or 17.11.6 right away.
“We strongly recommend that all installations running a version affected by the issues described below are upgraded to the latest version as soon as possible,” GitLab stated in its advisory.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind