Cyber Threat Intelligence Unit of BGD e-GOV CIRT found evidence of compromise linked to the vulnerability in F5 BIG-IP systems used in Bangladesh’s IT infrastructure. Investigators discovered that attackers gained shell access to the system and tried to sell this unauthorized access on the dark web. On October 30, one …
Read More »(CVE–2023-46747)
Google fixes two Android zero-days: Demand Immediate Patching
In its November 2024 security update, Google fixed 40 vulnerabilities in Android, including two that are actively exploited: CVE-2024-43047 and CVE-2024-43093. Google’s announcement gives minimal information about the exploitation, stating only that “there are indications that the following may be under limited, targeted exploitation.” CVE-2024-43047 is a critical vulnerability (CVSS …
Read More »Hikvision Patches Security Flaw in Network Cameras
Hikvision, a top provider of network cameras, has issued firmware updates to fix a security vulnerability that could reveal users’ Dynamic DNS credentials. This issue impacts various Hikvision camera models and may allow attackers to access sensitive information or disrupt camera communication with the Dynamic DNS service. The Vulnerability: Older …
Read More »Unprotected UN Database Exposes 228GB of Gender Violence Victims’ Data
Cybersecurity researcher Jeremiah Fowler found a non-password-protected database with 115,000 records linked to the UN Trust Fund to End Violence against Women. This fund aims to prevent violence against women and girls by supporting organizations that address gender-based violence and promote women’s rights. The unprotected database contained sensitive financial reports, …
Read More »Cisco Issues Urgent Fix for ASA and FTD Software Vulnerability
Cisco announced updates on Wednesday to fix a security flaw in its Adaptive Security Appliance (ASA) that is currently being exploited and could cause a denial-of-service (DoS) condition. CVE-2024-20481 (CVSS score: 5.8) is A vulnerability in the Remote Access VPN (RAVPN) service of Cisco Adaptive Security Appliance (ASA) Software and …
Read More »2nd time hacker breached Internet Archive
The Internet Archive was breached again, this time through their Zendesk email support platform, following warnings that threat actors had stolen exposed GitLab authentication tokens. Bleeping computer reported, Since last night, the authority received numerous messages from people who received replies to their old Internet Archive removal requests, warning that …
Read More »Vulnhuntr: A Tool for Finding Exploitable Vulnerabilities with LLMs
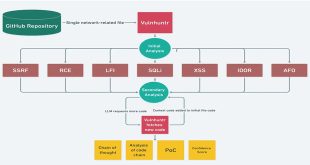
In today’s changing cybersecurity environment, it’s essential to find vulnerabilities in code. Vulnhuntr, an open-source tool on GitHub, uses Large Language Models (LLMs) and static code analysis to detect remotely exploitable vulnerabilities in Python projects. Its user-friendly design combines intelligent automation with thorough code analysis, making it a valuable resource …
Read More »Critical Vulnerabilities in Bitdefender Total Security Expose Users to MITM
Bitdefender said a vulnerability has been identified in Bitdefender Total Security HTTPS scanning functionality where the software fails to properly validate website certificates. Specifically, if a site certificate lacks the “Server Authentication” specification in the Extended Key Usage extension, the product does not verify the certificate’s compliance with the site, …
Read More »
CVE-2024-38814
VMware fixes high-severity SQL injection flaw in HCX
VMware has issued a warning about a remote code execution vulnerability, CVE-2024-38814, with a CVSS score of 8.8, in its HCX application mobility platform. An authenticated SQL injection vulnerability in HCX was privately reported to VMware by Sina Kheirkhah from the Summoning Team through the Trend Micro Zero Day Initiative. …
Read More »Over 90 Zero-Days, 40+ N-Days Exploited In The Wild
Mandiant researchers found that over 90 zero-day vulnerabilities and more than 40 known vulnerabilities were exploited in the wild. Vulnerabilities Exploited: A comprehensive vulnerability analysis by “Mandiant” for 2023 uncovered “138” actively exploited “security vulnerabilities.” They identified a significant prevalence of “97 zero-day vulnerabilities” and “41 n-day vulnerabilities” (the latter …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind