The Wall Street Journal reported on Friday citing people familiar with the matter that T-Mobile’s network was among the systems hacked in a damaging Chinese cyber-espionage operation that successfully gained entry into multiple U.S. and international telecommunications companies. Hackers were able to breach T-Mobile as part of a monthslong campaign …
Read More »WSJ reports
Palo Alto Networks Confirms critical RCE zero-day actively exploited
“Palo Alto Networks has observed threat activity exploiting an unauthenticated remote command execution vulnerability against a limited number of firewall management interfaces which are exposed to the Internet. We are actively investigating this activity,” reads the security bulletin by the cybersecurity provider Palo Alto Networks. On November 8, Palo Alto …
Read More »
(CVE-2024-52301)
Laravel Flaw Unveils Millions of Web Applications to Attack
A significant security flaw, CVE-2024-52301, has been found in the Laravel framework, which is widely used for web applications. With a CVSS rating of 8.7, this vulnerability could allow unauthorized access, data tampering, and privilege escalation in many Laravel applications. CVE-2024-52301 pertains to inadequate input validation in Laravel’s environment configuration. …
Read More »Microsoft November Patch Tuesday: 4 Zero-Days & 89 flaws
Microsoft’s latest Patch Tuesday update fixes 89 security vulnerabilities. Four of these are zero-day vulnerabilities, with two currently being exploited. This patch release highlights the need for timely updates to guard against cyber threats. Zero-Day Vulnerabilities Patched: The four zero-day vulnerabilities patched in this update include two that attackers have …
Read More »CISA Warns of 3 Critical Vulnerabilities in Industrial Control Systems
On November 7, 2024, CISA released advisories about 3 critical security issues, vulnerabilities, and exploits related to Industrial Control Systems (ICS). ICSA-24-312-01 Beckhoff Automation TwinCAT Package Manager: CISA has identified a serious vulnerability in Beckhoff Automation’s TwinCAT Package Manager, a key software in manufacturing. The flaw, called CVE-2024-8934, relates to …
Read More »Cyberattack Disrupts Israel’s Gas and Payment Systems
A cyberattack on an Israeli clearing company on Sunday left some people unable to use their credit cards for shopping for several hours. According to Times of Israel, The incident occurred less than two weeks after a similar attack briefly disrupted another credit services company. In Sunday’s incident, a DDoS …
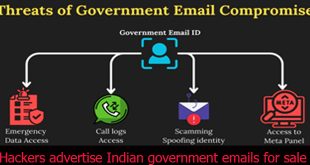
Read More »Hacker to sale Indian Gov.t email credentials
Advertisement for selling the credentials of allegedly belonging to Indian government emails surfaced on the dark web marketplace. A hacker on a private forum claims that purchasing access to these government email accounts can make anyone willing to pay a few thousand rupees “become” a government officer. The forum post …
Read More »Cyberattacks increase 105% in third quarter of 2024 in Bangladesh
Bangladesh faced a 105% rise in cyber incidents from the second to the third quarter of 2024, making it one of the countries with the fastest increase in cyberattacks. It ranks second after Japan (108%) and is closely followed by France (130%), underscoring significant cybersecurity challenges. The “Quarterly Threat Intelligence …
Read More »CISA alerts active exploitation of Palo Alto networks vuln
CISA has added a patched critical security flaw in Palo Alto Networks Expedition to its Known Exploited Vulnerabilities catalog due to signs of active exploitation. The vulnerability CVE-2024-5910 (CVSS score: 9.3) involves missing authentication in the Expedition migration tool, potentially allowing an admin account takeover. “Palo Alto Expedition contains a …
Read More »Critical bug in Cisco UWRB access points to run commands as root
Cisco has fixed a critical vulnerability, CVE-2024-20418, that allowed unauthenticated remote attackers to gain root access on Ultra-Reliable Wireless Backhaul (URWB) access points used in industrial wireless automation. The vulnerability is found in the web management interface of Cisco Unified Industrial Wireless Software for URWB Access Points. The vulnerability lets …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind