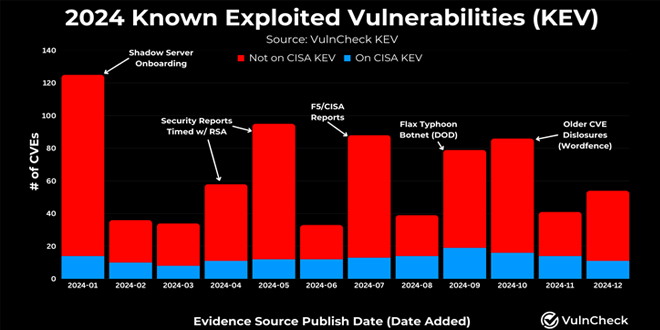
In 2024, 768 vulnerabilities with CVE identifiers were reported as exploited in the wild, a 20% increase from 639 in 2023. VulnCheck called 2024 “a strong year for threat actors exploiting vulnerabilities,” noting that 23.6% of known exploited vulnerabilities (KEVs) were weaponized by or on the day their CVEs were disclosed.
This represents a slight decrease from 2023’s 26.8%, showing that exploitation attempts can occur at any point in a vulnerability’s lifecycle.
By infosecbulletin
/ Saturday , May 31 2025
The Qualys Threat Research Unit (TRU) found two local information-disclosure vulnerabilities in Apport and systemd-coredump. Both issues are race-condition vulnerabilities....
Read More
By infosecbulletin
/ Saturday , May 31 2025
New ransomware payment reporting rules take effect in Australia yesterday (May 30) for all organisations with an annual turnover of...
Read More
By infosecbulletin
/ Saturday , May 31 2025
Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require...
Read More
By infosecbulletin
/ Thursday , May 29 2025
GreyNoise has discovered a campaign where attackers have gained unauthorized access to thousands of internet-exposed ASUS routers. This seems to...
Read More
By infosecbulletin
/ Wednesday , May 28 2025
The rise of online gambling in the country is leading to increased crime and societal issues. In response, the central...
Read More
By infosecbulletin
/ Wednesday , May 28 2025
Cybersecurity researchers recently revealed a coordinated cloud-based scanning attack that targeted 75 different exposure points earlier this month. On May...
Read More
By infosecbulletin
/ Monday , May 26 2025
Recent security research has shown that attackers can weaken zero-trust security frameworks by exploiting a key DNS vulnerability, disrupting automated...
Read More
By infosecbulletin
/ Saturday , May 24 2025
Evaly, a Bangladeshi e-commerce platform, is reportedly facing a major data breach that may have exposed sensitive information of around...
Read More
By infosecbulletin
/ Friday , May 23 2025
A passback vulnerability has been found in some Canon printers, including production and multifunction models. If an attacker gains administrative...
Read More
By infosecbulletin
/ Friday , May 23 2025
Security researchers have discovered a database with 184 million account credentials, highlighting the need to update compromised passwords, strengthen weak...
Read More
“During 2024, 1% of the CVEs published were reported publicly as exploited in the wild,” VulnCheck’s Patrick Garrity said. “This number is expected to grow as exploitation is often discovered long after a CVE is published.”
The report comes over two months after the company disclosed that 15 of 60 identified Chinese hacking groups are connected to the exploitation of at least one of the top 15 commonly exploited vulnerabilities in 2023.
“Not surprisingly, the Log4j CVE (CVE-2021-44228) is associated with the most threat actors overall, with 31 named threat actors linked to its exploitation,” Garrity noted late last year, adding the company identified 65,245 hosts potentially vulnerable to the flaw.
Approximately 400,000 internet-accessible systems may be vulnerable to attacks due to 15 security flaws in products from companies like Apache, Atlassian, Barracuda, Citrix, Cisco, Fortinet, Microsoft, Progress, PaperCut, and Zoho.
“Organizations should evaluate their exposure to these technologies, enhance visibility into potential risks, leverage robust threat intelligence, maintain strong patch management practices, and implement mitigating controls, such as minimizing internet-facing exposure of these devices wherever possible,” VulnCheck said.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind