Cisco fixed a critical vulnerability in the Identity Services Engine (ISE) that could let unauthorized attackers carry out harmful actions. The vulnerability, CVE-2025-20286 (CVSS score 9.9), affects Cisco ISE on AWS, Microsoft Azure, and Oracle Cloud. It allows unauthenticated remote attackers to access sensitive data, perform basic admin tasks, modify configurations, or disrupt services.
A vulnerability in Cisco ISE cloud deployments allows multiple instances with the same software version and cloud platform (AWS, Azure, or OCI) to share identical login credentials. This enables an attacker to extract credentials from one instance and access others, risking sensitive data, altering settings, or disrupting services.
Affected Products:
Vulnerable Products
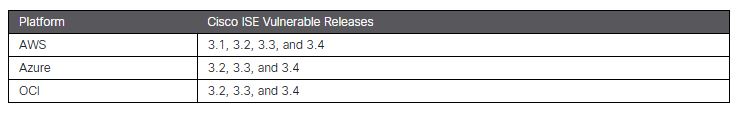
This vulnerability impacts specific versions of Cisco ISE in the default setup on AWS, Azure, and OCI platforms:
“This vulnerability exists because credentials are improperly generated when Cisco ISE is being deployed on cloud platforms, resulting in different Cisco ISE deployments sharing the same credentials. These credentials are shared across multiple Cisco ISE deployments as long as the software release and cloud platform are the same. An attacker could exploit this vulnerability by extracting the user credentials from Cisco ISE that is deployed in the cloud and then using them to access Cisco ISE that is deployed in other cloud environments through unsecured ports.” reads the advisory. “A successful exploit could allow the attacker to access sensitive data, execute limited administrative operations, modify system configurations, or disrupt services within the impacted systems.”
Kentaro Kawane from GMO Cybersecurity found a vulnerability that Cisco PSIRT confirmed. They noted that proof-of-concept code exists, but there’s no evidence of it being exploited in real-world attacks.
There is no direct workaround for the Cisco Identity Services Engine cloud vulnerability, but Cisco has offered important mitigations for administrators. First, restrict access to trusted source IP addresses using cloud security groups or the Cisco Identity Services Engine interface.
For new installations, Cisco suggests using the command application reset-config ise on the cloud-based primary node to create new credentials.
Note: this will reset the system to factory settings, and restoring from a backup will bring back the original (potentially vulnerable) credentials.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind