Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The company found the issue during internal security tests and has issued a firmware update to fix it.
An attacker with network access to the access point’s management IP can bypass authentication. This exploit provides them with administrator privileges on the device.
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
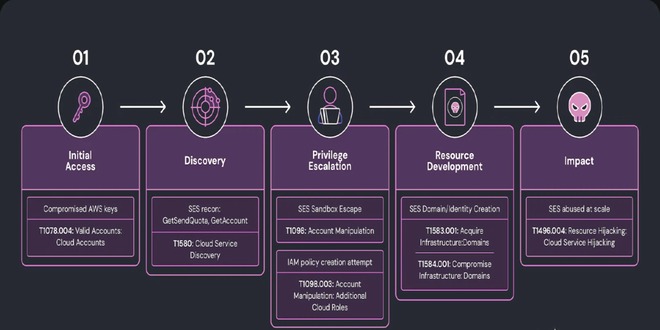
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
By infosecbulletin
/ Sunday , September 7 2025
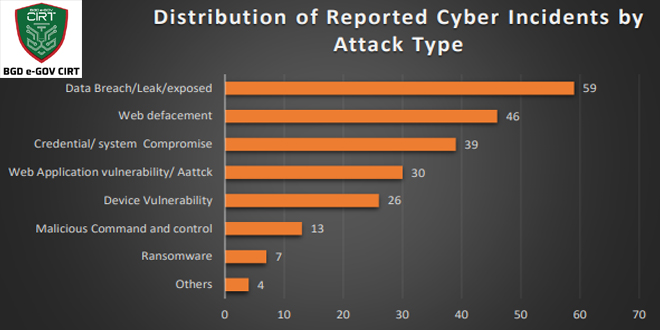
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year...
Read More
By infosecbulletin
/ Sunday , September 7 2025
Investigations into the Nx "s1ngularity" NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and...
Read More
By infosecbulletin
/ Saturday , September 6 2025
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR)...
Read More
This elevated access can help control the access point, intercept or change network traffic, disrupt wireless connections, or use the compromised device to launch further attacks.
Sophos reported that the vulnerability was found by its own team, highlighting a proactive approach to product security. The nature of the flaw, requiring access to the management interface, suggests that the primary risk is from attackers already on the local network.
Sophos Wireless Access Points Vulnerability:
Sophos AP6 Series Wireless Access Points with firmware versions before 1.7.2563 (MR7) have a vulnerability. A fix is available in firmware version 1.7.2563 (MR7), released after August 11, 2025.
Administrators should check that their access points are using this version or a newer one for protection. Organizations using old firmware are at risk and need to upgrade for security fixes to protect their networks.
Most customers have an automatic remediation process. Sophos AP6 devices are set up to install updates automatically, so patched firmware is applied without any manual effort.
This policy helps most users stay protected automatically. However, those who chose not to receive updates need to update manually. Users must upgrade their AP6 Series firmware to version 1.7.2563 (MR7) or newer to apply the patch.
While Sophos has indicated that no exploitation has been observed in the wild, the high CVSS score of 9.8 reflects the seriousness of the vulnerability and the potential damage if left unpatched.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind