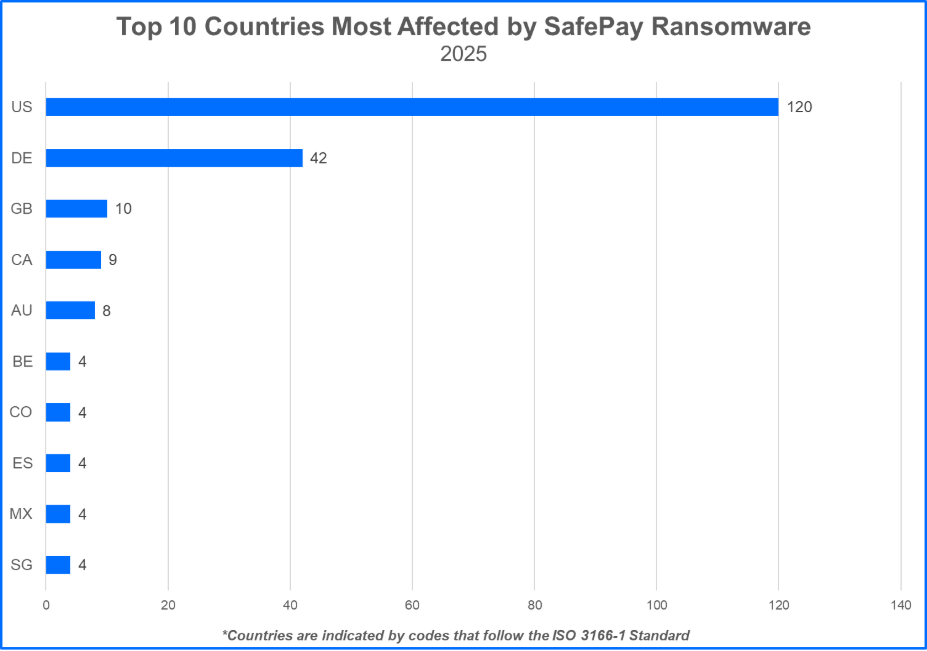
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and disruptive groups. In June, SafePay claimed responsibility for attacks on 73 victim organizations, a record-breaking monthly tally that placed it at the top of Bitdefender’s Threat Debrief rankings.
The surge has continued, with another 42 victims published in July, marking SafePay’s second-highest tally to date. So far in 2025, the group has publicly named more than 270 victim organizations.
SafePay first surfaced in September 2024, several months after law enforcement dismantled the major ransomware players LockBit and ALPHV/BlackCat. While researchers have traceable evidence of code similarities to LockBit Black, SafePay has charted a distinct course.
It rejects the ransomware-as-a-service (RaaS) model, instead keeping its operations closed—a strategy that minimizes exposure, strengthens operational security, and ensures that the group retains all profits.
Unlike RaaS operators who rely on affiliates, SafePay conducts its own attacks against mid-sized and enterprise organizations, deliberately targeting partners within sprawling supply chains.
Its top victim demographics include companies in the U.S., Germany, the U.K., and Canada, with industries like manufacturing, healthcare, and construction being prime targets.
A 24-Hour Blitzkrieg:
One hallmark of SafePay’s campaign has been its capacity to claim dozens of victims in a single day. On multiple occasions, it has published more than 10 organizations on its leak site within 24 hours, most notably 29 victims on March 30, 2025. This rivals even large affiliate-driven groups such as Qilin and Akira.
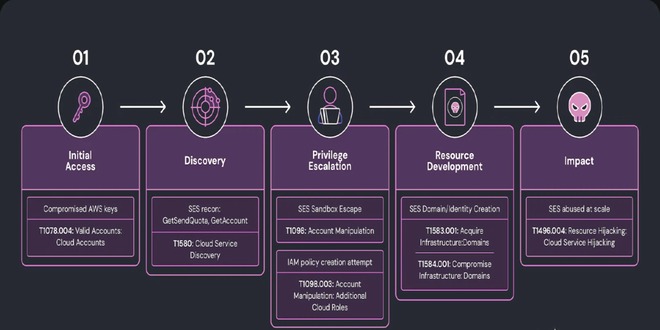
The key to this productivity lies in SafePay’s tactics, techniques, and procedures (TTPs). For initial access, the group leverages compromised credentials, brute-force attacks, or vulnerabilities in VPN appliances, occasionally bolstered by social engineering where attackers impersonate IT staff.
Once inside, discovery scripts like ShareFinder.ps1 allow them to locate sensitive network shares. Lateral movement is facilitated via PsExec, before exfiltration begins using tools such as WinRAR and FileZilla.
Encryption is handled by the ChaCha20 algorithm, with each file assigned a unique symmetric key. Files receive the “.safepay” extension, and ransom notes titled readme_safepay.txt direct victims to negotiate over Tor.
SafePay demands vary widely, often calculated against an organization’s revenue, with some victims exceeding $100M in turnover.
Researchers also note deliberate defense evasion measures, including debugger bypasses and process termination against security tools. The ransomware avoids execution on systems configured with Cyrillic keyboards, an indicator of possible Russian ties or alliances.
The Larger Picture:
While SafePay does not interact with other threat actors or sell stolen data on underground forums, its streamlined operations and rapid-fire disclosures signal a new breed of ransomware group that thrives without affiliates.
Safepages contact Page:
Its efficiency, discretion, and aggressive publishing cadence have made it one of 2025’s most concerning ransomware threats, underscoring the urgent need for defenders to adopt multi-layered security, rapid patching, and proactive monitoring against this accelerating menace.
602 Vuln exploited: Afftected daily 905 IP In Bangladesh in 2024 – InfoSecBulletin
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind