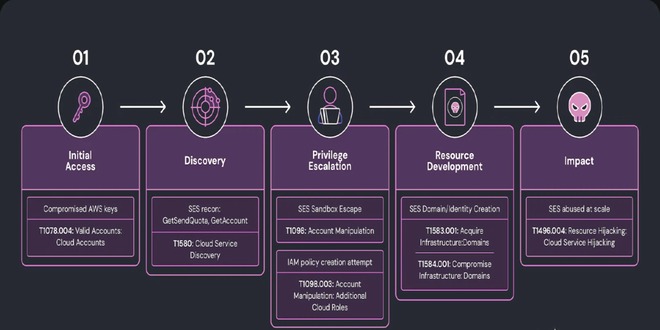
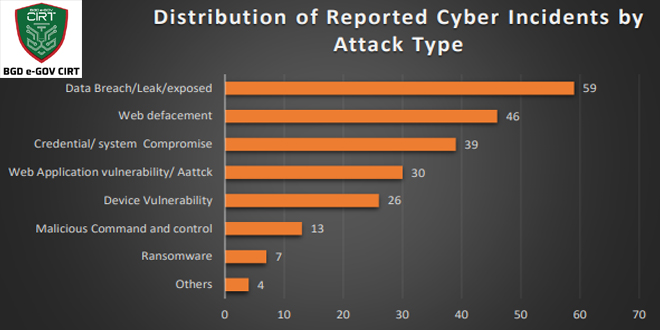
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical vulnerabilities: five for remote code execution, one for information disclosure, and two for privilege escalation.
The number of bugs in each vulnerability category is listed below:
41 Elevation of Privilege Vulnerabilities
2 Security Feature Bypass Vulnerabilities
22 Remote Code Execution Vulnerabilities
16 Information Disclosure Vulnerabilities
3 Denial of Service Vulnerabilities
1 Spoofing Vulnerabilities
Two publicly disclosed zero-days fixed:
This month’s Patch Tuesday addresses two zero-day vulnerabilities in Windows SMB Server and Microsoft SQL Server. A zero-day vulnerability is one that is publicly known or exploited without an official fix.
The two publicly disclosed zero-days are:
CVE-2025-55234 – Windows SMB Elevation of Privilege Vulnerability:
Microsoft patched a vulnerability in SMB Server that could be exploited through relay attacks.
“SMB Server might be susceptible to relay attacks depending on the configuration. An attacker who successfully exploited these vulnerabilities could perform relay attacks and make the users subject to elevation of privilege attacks,” explains Microsoft.
Microsoft states that Windows includes settings to strengthen the SMB Server against relay attacks, such as enabling SMB Server Signing and Extended Protection for Authentication (EPA).
However, enabling these features could cause compatibility issues with older devices and implementations. Microsoft advises admins to enable auditing on SMB servers to identify potential issues before fully implementing hardening features.
“As part of the Windows updates released on and after September 9, 2025 (CVE-2025-55234), support is enabled for auditing SMB client compatibility for SMB Server signing as well as SMB Server EPA,” explains Microsoft.
CVE-2024-21907 – VulnCheck: CVE-2024-21907 Improper Handling of Exceptional Conditions in Newtonsoft.Json:
Microsoft has resolved a known issue in Newtonsoft.Json used by SQL Server. “CVE-2024-21907 addresses a mishandling of exceptional conditions vulnerability in Newtonsoft.Json before version 13.0.1,” explains Microsoft.
“Crafted data that is passed to the JsonConvert.DeserializeObject method may trigger a StackOverflow exception resulting in denial of service. Depending on the usage of the library, an unauthenticated and remote attacker may be able to cause the denial-of-service condition.”
“The documented SQL Server updates incorporate updates in Newtonsoft.Json which address this vulnerability.” This flaw was publicly disclosed in 2024.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind