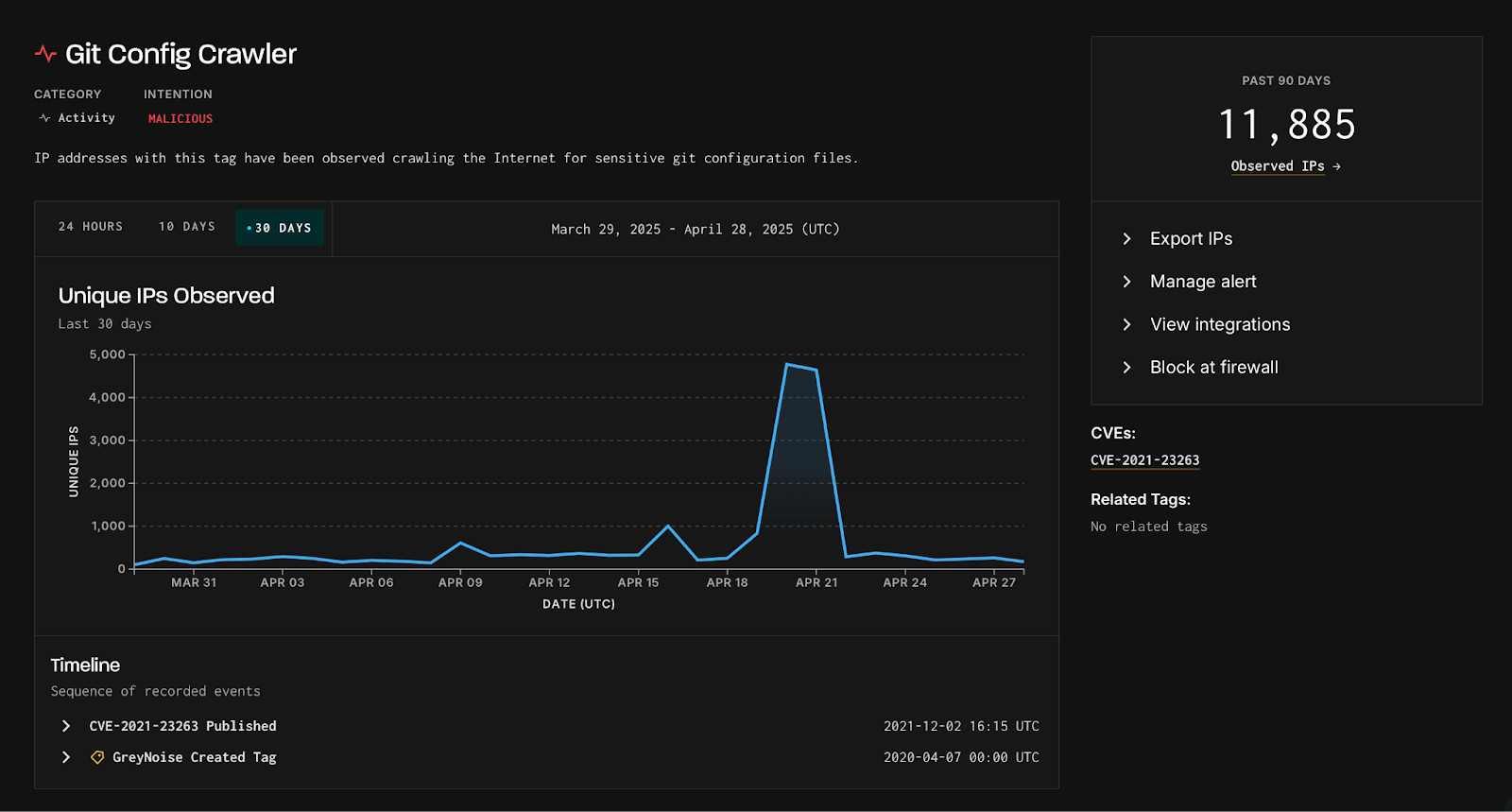
A recent increase in cyber reconnaissance has endangered thousands of organizations, as GreyNoise, a global threat intelligence platform, reported a significant rise in attempts to access sensitive Git configuration files.
On April 20 and 21, GreyNoise recorded over 4,800 unique IPs targeting these files, marking a record high and indicating increased interest from malicious actors.
CVE Spotlight: CVE-2021-23263:
This recent activity is not linked to a new zero-day vulnerability, but experts warn that attackers might take advantage of known issues like CVE-2021-23263 in certain web server setups that can accidentally reveal .git directories.
GreyNoise reports that this is the fourth and largest spike in Git configuration file crawling since September 2024, significantly exceeding earlier spikes that involved around 3,000 unique IPs.
Exposing a Git configuration file (or, worse, the entire .git/ directory) can reveal:
Remote repository URLs (e.g., GitHub, GitLab)
Branch structures and naming conventions
Insider metadata about development processes
Credentials embedded in commit history
To prevent such breaches:
Ensure .git/ directories are not web-accessible.
Block access to hidden files/folders in web server configs.
Monitor server logs for repeated requests to .git/config.
Immediately rotate any exposed credentials.
Blocking malicious IPs and closing these gaps should be a top priority for any organization relying on Git for source code management.
If exploited, attackers can download the entire Git repository, including its configuration files, commit history, and sensitive credentials.
Malicious IPs and Regional Targeting:
95% of IPs involved in this behavior over the past 90 days are classified as malicious, highlighting a significant threat to exposed sites. While this activity is widespread, it is particularly concentrated in Asia, with Singapore identified as the leading source and destination for these scanning sessions, followed by the U.S. and Germany.
Top Source Countries (Unique IPs):
Singapore: 4,933
U.S.: 3,807
Germany: 473
U.K.: 395
Netherlands: 321
Top Destination Countries (Unique IPs):
Singapore: 8,265
U.S.: 5,143
Germany: 4,138
U.K.: 3,417
India: 3,373
Greynoise report claimed, the IPs are linked to cloud infrastructure providers such as Cloudflare, Amazon, and DigitalOcean.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind