On September 1, 2025, Qrator Lab identified and managed a major attack from the largest L7 DDoS botnet seen so far, targeting a government organization. A total of 5.76 million IP addresses were blocked.
Qrator Labs has been tracking a botnet for months. The first attack occurred on March 26, targeting an online betting organization and involving approximately 1.33 million IP addresses, mainly from Brazil, Argentina, Russia, Iraq, and Mexico.
By infosecbulletin
/ Thursday , September 11 2025
On September 1, 2025, Qrator Lab identified and managed a major attack from the largest L7 DDoS botnet seen so...
Read More
By infosecbulletin
/ Thursday , September 11 2025
A new vulnerability, CVE-2025-4235, in Palo Alto Networks’ User-ID Credential Agent for Windows, could reveal a service account's password in...
Read More
By infosecbulletin
/ Thursday , September 11 2025
CyberVolk ransomware, which appeared in May 2024, has increased attacks on government agencies and critical infrastructures in Japan, France, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
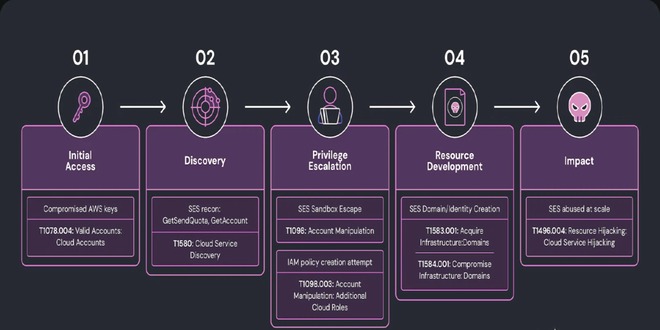
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
On May 16, a second incident affected a government organization, with the botnet growing to 4.6 million devices. Most traffic came from Brazil, the U.S., Vietnam, India, and Argentina.
By September, the botnet grew larger. The third attack targeted the government sector with 5.76 million IP addresses involved. It occurred in two phases: the first wave had about 2.8 million IP addresses, followed by an additional 3 million an hour later.
Most malicious traffic originated from Brazil (1.41M), Vietnam (661K), the U.S. (647K), India (408K), and Argentina (162K). Over three months, the biggest increases in botnet participation were seen in Vietnam (+83%) and India (+202%).
“When targeting unprotected or poorly protected resources, a DDoS botnet of this scale can generate tens of millions of requests per second, overwhelming servers within minutes. What’s more, not every DDoS protection provider is capable of withstanding such a massive attack, which means the availability of all their clients’ resources could be at risk simultaneously,” said Andrey Leskin, CTO at Qrator Labs.
CyberVolk Ransomware Attacks CII In Japan, France, and UK – InfoSecBulletin
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind