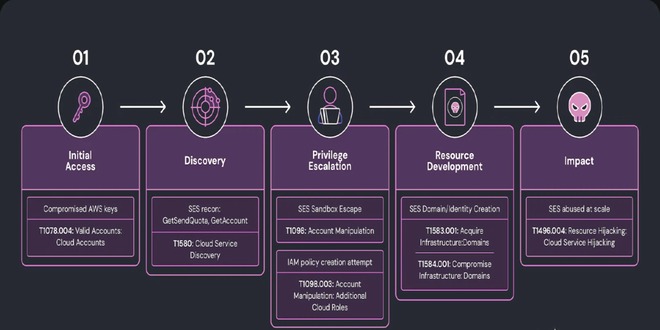
Researchers at Wiz discovered a complex phishing campaign using Amazon’s Simple Email Service (SES) for large-scale attacks, showing how hacked cloud credentials can evade standard email security measures.
The attack, identified in May 2025, began with stolen AWS access keys a common attack vector that Wiz observes “tens of newly compromised cloud access keys each month.”
the attacker’s careful strategy to increase their email sending abilities from limited “sandbox” mode to full production access.
From Sandbox to Production: A Technical Breakdown:
Amazon SES has strict rules for new accounts, allowing only 200 emails a day to verified addresses.
The attacker confirmed their stolen credentials had SES permissions and then launched a rapid automated attack across all AWS regions using PutAccountDetails requests. This technique was previously undocumented.
“Within a span of just ten seconds, we observed a burst of PutAccountDetails requests that fanned out across all AWS regions,” the Wiz research team noted. This automation successfully convinced AWS support to approve the account for production mode, removing sending restrictions and increasing the daily quota to 50,000 emails.
The attacker used a seemingly normal explanation from a construction company to successfully pass AWS’s review.
When efforts to boost limits via support tickets failed due to permission issues, the threat actor moved ahead with the 50,000-email capacity.
Infrastructure and Impact:
The campaign set up a complex phishing setup using both attacker-owned domains (managed7.com, street7news.org, street7market.net, docfilessa.com) and weakly protected legitimate domains.
Email addresses were created using common business prefixes like admin@, billing@, and sales@, lending credibility to the malicious messages.
A phishing campaign targeted various organizations with tax-related emails, such as “Your 2024 Tax Form(s) Are Now Ready to View and Print,” leading victims to credential theft sites. The attackers used commercial traffic analysis to bypass security scanners and track engagement rates.
The attack shows serious weaknesses in cloud security. Besides the phishing risk, SES abuse can lead to reputational harm, operational issues from complaints, and signals a larger issue of AWS credential theft.
Organizations can protect against attacks by using Service Control Policies to block unused SES access, regularly rotating IAM keys, enforcing least-privilege principles, and monitoring CloudTrail logs for suspicious activities like unusual PutAccountDetails requests and sender identity additions.
The campaign shows that attackers are using legitimate cloud services for large operations, shifting costs and damage to their victims.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind