CyberVolk ransomware, which appeared in May 2024, has increased attacks on government agencies and critical infrastructures in Japan, France, and the UK. CyberVolk, with pro-Russian views, targets countries seen as threats to Russia using advanced encryption that is very hard to break.
This article analyzes CyberVolk’s encryption system, its execution process, and the flaws that hinder recovery without backups.
CyberVolk emerged in May 2024, targeting public sectors in countries with anti-Russian stances. The group uses Telegram to send threats and ransom demands to victims. Notable attacks include Japanese power grids, French research labs, and British scientific groups.
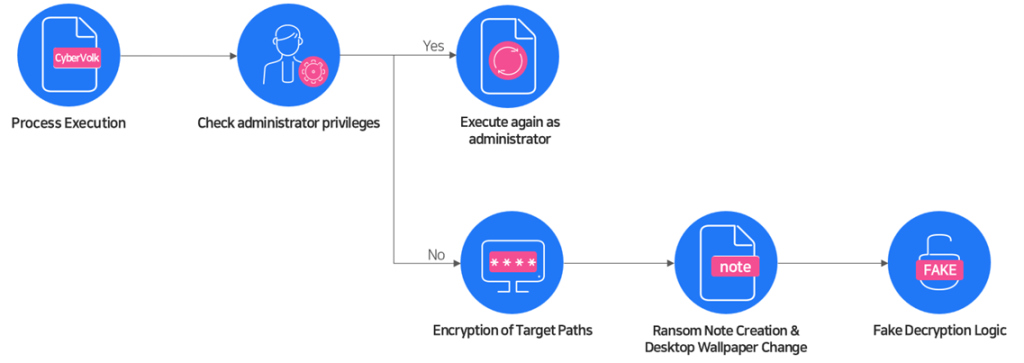
CyberVolk seems motivated by geopolitical reasons, supporting pro-Russian views by undermining the technology of rival countries. The ransomware starts with standard user privileges but then runs again with administrator rights to access the entire system.
It then builds an exclusion list to avoid destabilizing critical system directories. Paths containing substrings—such as “Windows,” “Program Files,” and “ProgramData”—are omitted from encryption to maintain system stability and enable persistence after reboot.
Encryption Exclusions:
CyberVolk ignores files with its custom extension and system folders to avoid redundancy and reinfection.
Windows.
Program Files.
ProgramData.
CyberVolk.
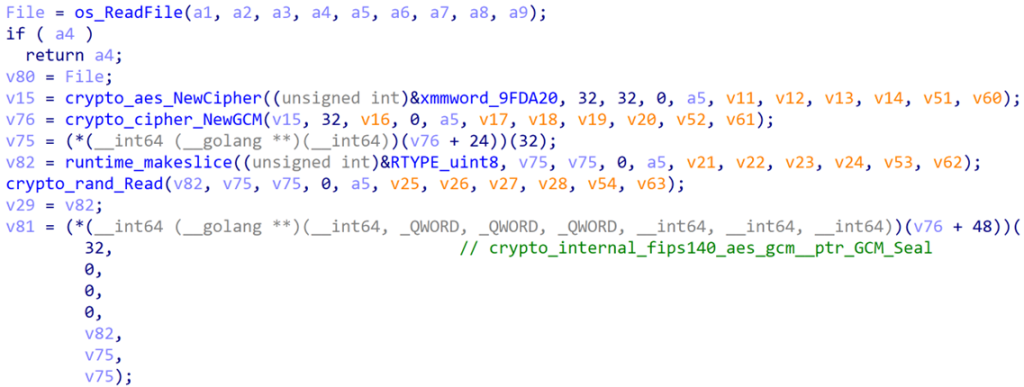
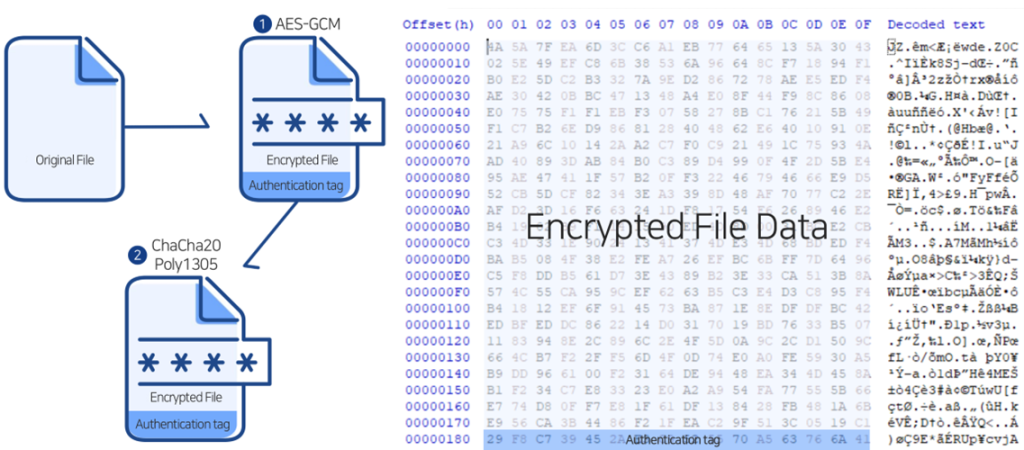
The ransomware uses a two-layer symmetric encryption method with AES-256 GCM and ChaCha20-Poly1305. A single symmetric key is generated at process initialization and applied uniformly across all target files. Each file encryption begins with a 12-byte nonce produced by crypto_rand_Read().
This nonce guarantees unique ciphertexts for the same plaintexts. The file is first encrypted with AES-256 GCM, generating ciphertext and an authentication tag, then encrypted again using ChaCha20-Poly1305.
File Structure Changes:
Post-encryption files only contain encrypted data and the ChaCha20-Poly1305 authentication tag, with no nonce or key metadata saved alongside the ciphertext. As a result, offline decryption is impossible.
After encryption, the ransomware creates a ransom note called READMENOW.txt in the execution folder. A desktop background change and a note prompt victim to enter a fixed decryption key within three tries.
Decryption logic exists but mishandles the nonce, leading to decryption errors. CyberVolk’s ransomware uses strong double-layer encryption with unique, non-storable random values, ensuring that the encrypted data can’t be recovered.
Its pro-Russian orientation and selective targeting of anti-Russian states underscore the geopolitical dimension of its cyber assaults. Organizations need strong backup strategies, keeping offline and controlled copies of important data, and should regularly practice recovery drills to prevent data loss.
Securing backup systems is essential for maintaining operational continuity.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind